What is CVSS
The Common Vulnerability Scoring System (CVSS) is a standardized method for assessing and quantifying the severity of security vulnerabilities. It provides a numerical score, ranging from 0 to 10. The CVSS score considers various factors, including the ease of exploitation, the impact on confidentiality, integrity, and availability, as well as whether the vulnerability requires user interaction. A higher score indicates a more severe vulnerability.
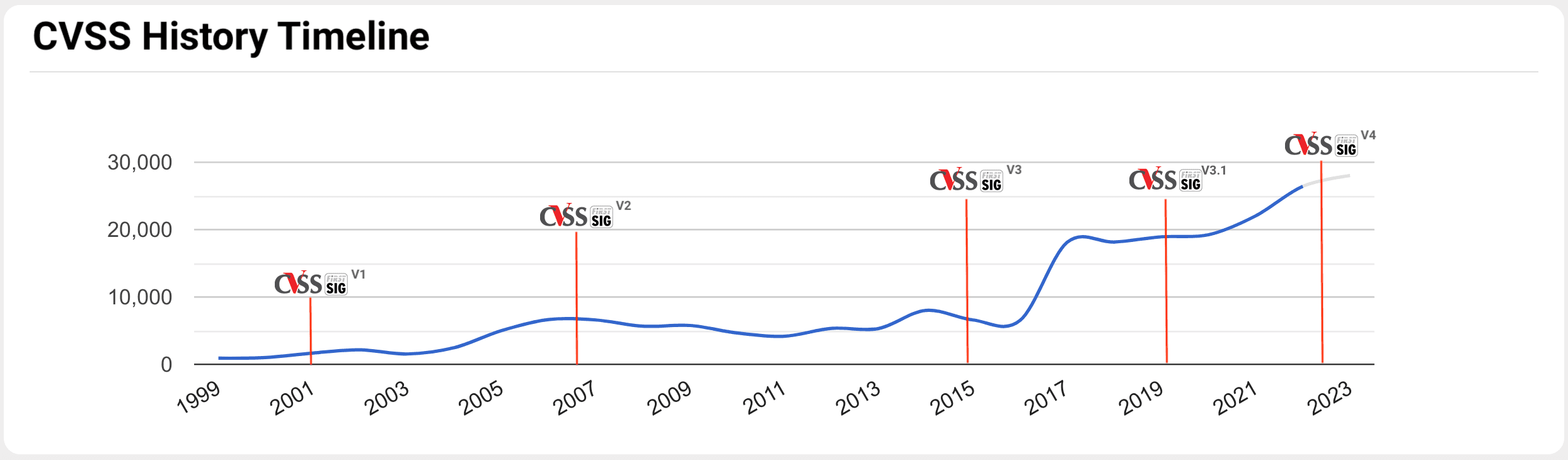
In the illustration provided below, we showcase the chronological progression and historical timeline of the Common Vulnerability Scoring System open framework.
The Problem
With a significant daily influx of vulnerabilities, the assessment and assignment of CVSS base scores typically demand considerable time, expertise, and human resources. We have observed public CVEs where vulnerabilities appeared without a corresponding CVSS base scores. We have encountered PSIRT teams managing numerous vulnerabilities for the software they develop, and due to the volume of vulnerabilities they face, conducting a CVE assessment is hard and expensive. Ultimately, the PRIOn prioritization vulnerability algorithm considers the vulnerability's severity as one of the many supported features, making it part of the algorithm to receive this information, which cannot be left blank.
PRIOn KB NLP Models CVSS Prediction
Due to all the reasons described in the "The Problem" section, PRIOn has decided to build multiple Natural Language Processing (NLP) models which automates the prediction of the CVSS Base Vectors (not temporal, not environmental) and their corresponding severity scores, for both CVSSv2 and CVSSv3, solely based on textual vulnerability descriptions. Models take a vulnerability description as input and produce a CVSS vector/base score as output using the relevant CVSS (V2/V3) metrics. We created multiple datasets for solving this problem. We utilized a CVSSv3 corpus containing 137,353 CVE documents and a CVSSv2 corpus containing 175,126 CVE documents. We conducted deduplication and performed some cleaning steps on those corpora. In the subsequent images, we conducted analyses on all CVEs, both CVSSv2 and CVSSv3, respectively.
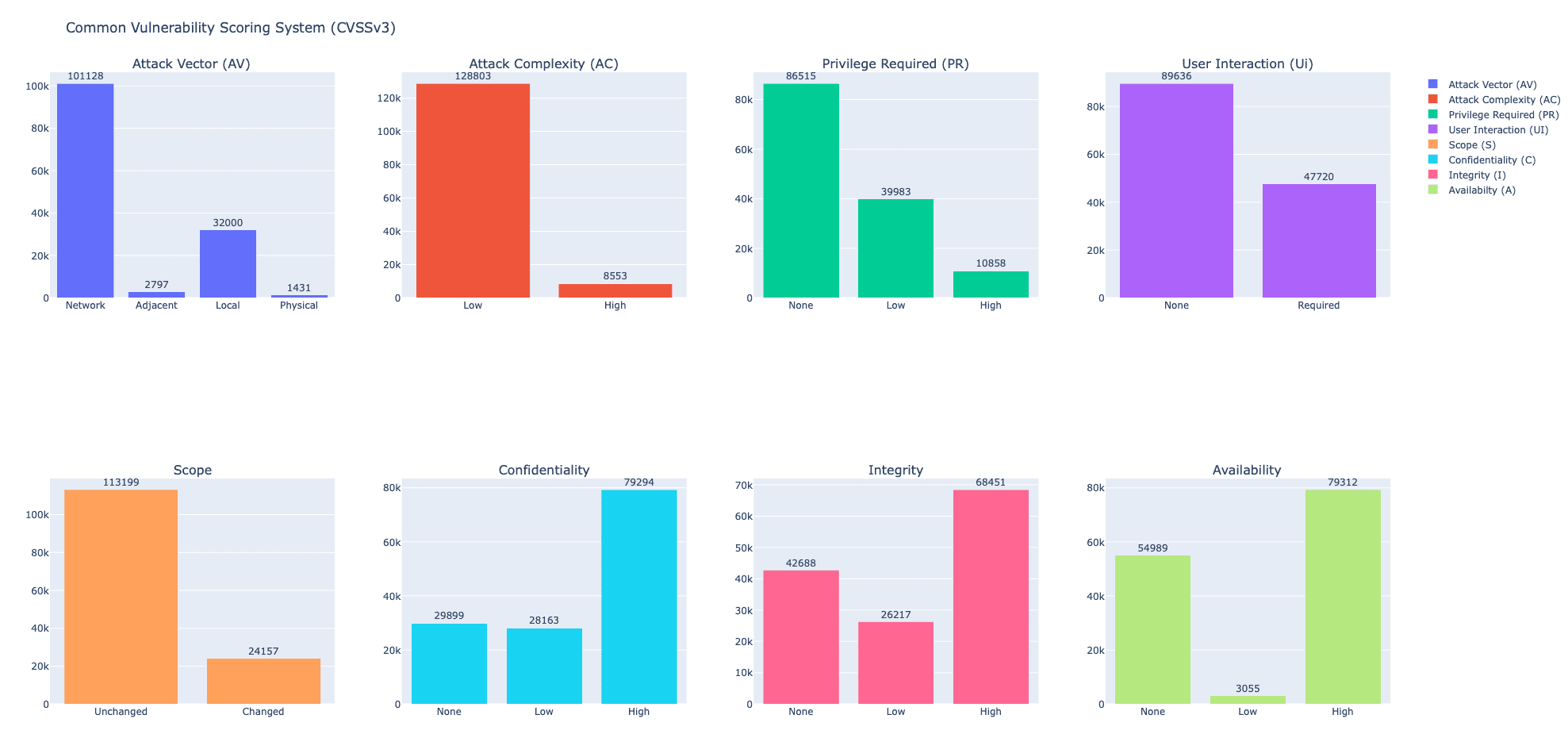
CVSSv3 Metrics and Values
The table below presents a collection of metrics associated with the Base metric group:
Metric | Values |
Attack Vector (AV) | Network, Adjacent, Local, Physical |
Attack Complexity (AC) | Low, High |
Privilege Required (PR) | None, Low, High |
User Interaction (UI) | None, Required |
Score | Unchanged, Changed |
Confidentiality | None, Low, High |
Integrity | None, Low, High |
Availability | None, Low, High |
Exploratory Data Analysis on CVSSv3 corpus.
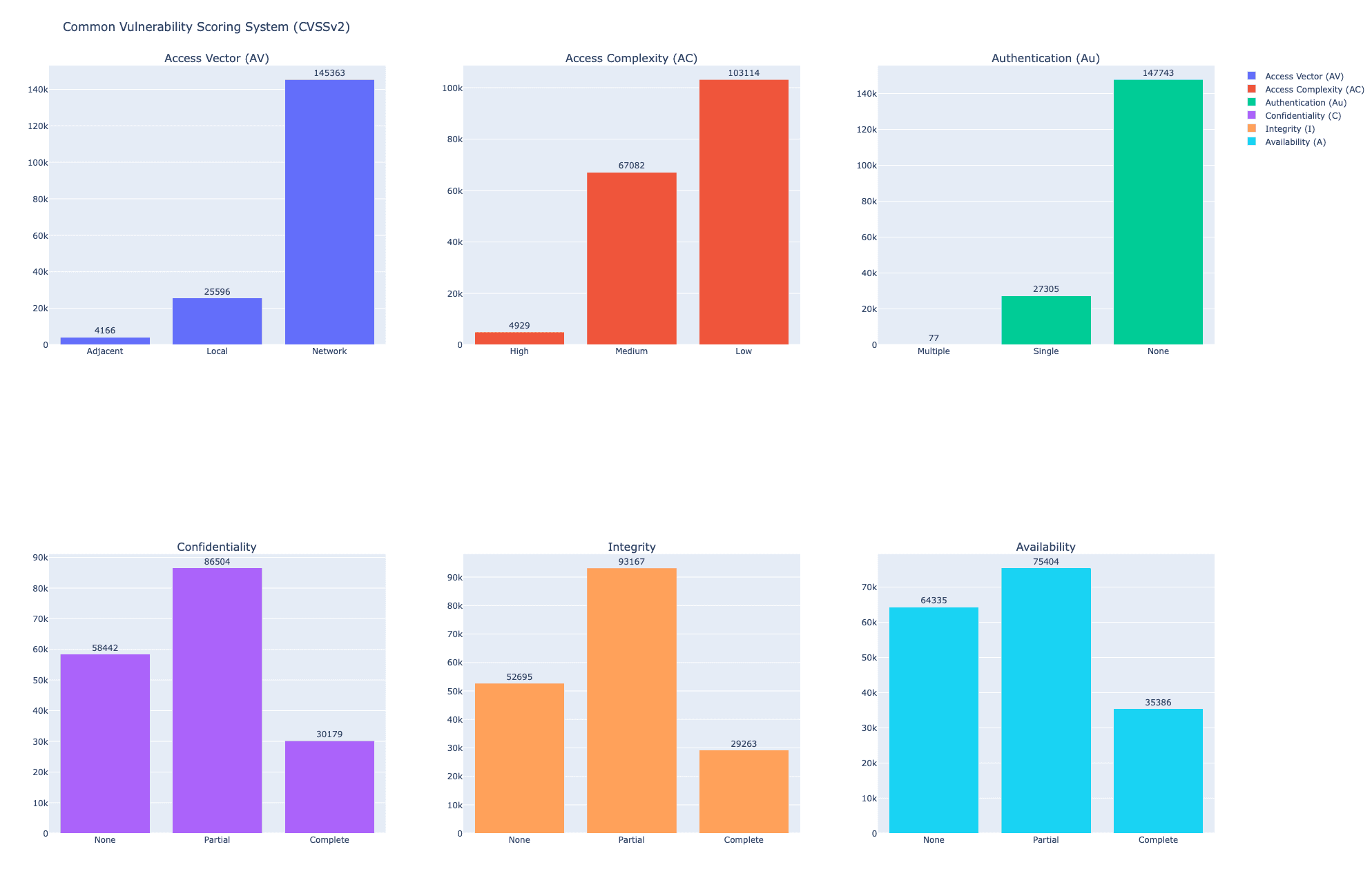
CVSSv2 Metrics and Values
The table below presents a collection of metrics associated with the Base metric group:
Metric | Values |
Access Vector (AV) | Network, Adjacent, Local |
Access Complexity (AC) | Low, Medium, High |
Authentication (Au) | None, Single, Multiple |
Confidentiality | None, Partial, Complete |
Integrity | None, Partial, Complete |
Availability | None, Partial, Complete |
Exploratory Data Analysis on CVSSv2 corpus.
CVSSv3 Model Performance Evaluation
In the table provided, we illustrate the CVSSv3 model's overall accuracy performance score (94.33) and the performance for each specific CVSSv3 metric, measured in terms of AUC (Area Under the ROC Curve), precision (P), recall (R), and F1 score (F).
Score: 94.33 | ||||
Metrics | Precision | Recall | F1-Score | ROC AUC |
AttackVector: Network | 94.23 | 95.44 | 94.83 | 0.96 |
AttackVector:Adjacent | 80.79 | 43.84 | 56.84 | 0.90 |
AttackVector:Local | 86.41 | 85.41 | 85.91 | 0.97 |
AttackVector:Physical | 87.93 | 51.78 | 65.18 | 0.94 |
AttackComplexity:Low | 96.63 | 99.36 | 97.98 | 0.90 |
AttackComplexity:High | 83.29 | 49.53 | 62.12 | 0.90 |
PrivilegeRequired:None | 89.47 | 91.76 | 90.60 | 0.93 |
PrivilegeRequired:Low | 79.77 | 74.30 | 76.94 | 0.92 |
PrivilegeRequired:High | 83.46 | 61.02 | 70.50 | 0.92 |
UserInteraction:None | 93.70 | 96.80 | 95.23 | 0.97 |
UserInteraction:Required | 93.70 | 88.28 | 90.91 | 0.97 |
Scope:Unchanged | 96.70 | 99.36 | 98.01 | 0.96 |
Scope:Changed | 96.61 | 83.83 | 89.77 | 0.96 |
Confidentiality:None | 90.56 | 76.24 | 82.79 | 0.96 |
Confidentiality:Low | 89.12 | 77.79 | 83.07 | 0.96 |
Confidentiality:High | 88.32 | 93.34 | 90.76 | 0.95 |
Integrity:None | 88.21 | 87.09 | 87.65 | 0.97 |
Integrity:Low | 93.38 | 80.84 | 86.66 | 0.97 |
Integrity:High | 89.67 | 90.41 | 90.04 | 0.96 |
Availability:None | 88.09 | 89.04 | 88.56 | 0.97 |
Availability:Low | 90.62 | 25.00 | 39.19 | 0.82 |
Availability:High | 91.65 | 91.54 | 91.59 | 0.96 |
CVSSv2 Model Performance Evaluation
In the table provided, we illustrate the CVSSv2 model's overall accuracy performance score (93.90) and the performance for each CVSSv2 metric, measured in terms of AUC (Area Under the ROC Curve), precision (P), recall (R), and F1 score (F).
Score: 93.90 | ||||
Metrics | Precision | Recall | F1-Score | RoC AUC |
AccessVector:Local | 89.25 | 84.94 | 87.04 | 0.98 |
AccessVector:Network | 96.64 | 98.22 | 97.42 | 0.97 |
AccessVector:Adjacent | 94.88 | 54.56 | 69.28 | 0.92 |
AccessComplexity:High | 92.14 | 16.39 | 27.83 | 0.81 |
AccessComplexity:Medium | 85.49 | 80.26 | 82.79 | 0.92 |
AccessComplexity:Low | 87.16 | 92.02 | 89.53 | 0.93 |
Authentication:Single | 83.00 | 73.12 | 77.74 | 0.95 |
Authentication:None | 95.11 | 97.27 | 96.18 | 0.95 |
ConfidentialityImpact:None | 90.69 | 86.51 | 88.55 | 0.97 |
ConfidentialityImpact:Partial | 84.24 | 86.25 | 85.23 | 0.93 |
ConfidentialityImpact:Complete | 78.47 | 67.95 | 72.84 | 0.94 |
IntegrityImpact:None | 90.17 | 88.28 | 89.21 | 0.97 |
IntegrityImpact::Partial | 87.45 | 88.32 | 87.89 | 0.94 |
IntegrityImpact:Complete | 78.41 | 70.72 | 74.37 | 0.95 |
AvailabilityImpact:None | 89.55 | 88.77 | 89.16 | 0.97 |
AvailabilityImpact:Partial | 81.30 | 81.45 | 81.38 | 0.92 |
AvailabilityImpact:Complete | 78.02 | 68.57 | 72.99 | 0.93 |
Case Study: CVE-2023-6359 (Cross Site Scripting)
In the provided image, it's evident that the vulnerability CVE-2023-6359 remains indeterminate. PRIOn Basic analysis can predict the CVSSv2 and CVSSv3 base scores for the CVE description under examination.
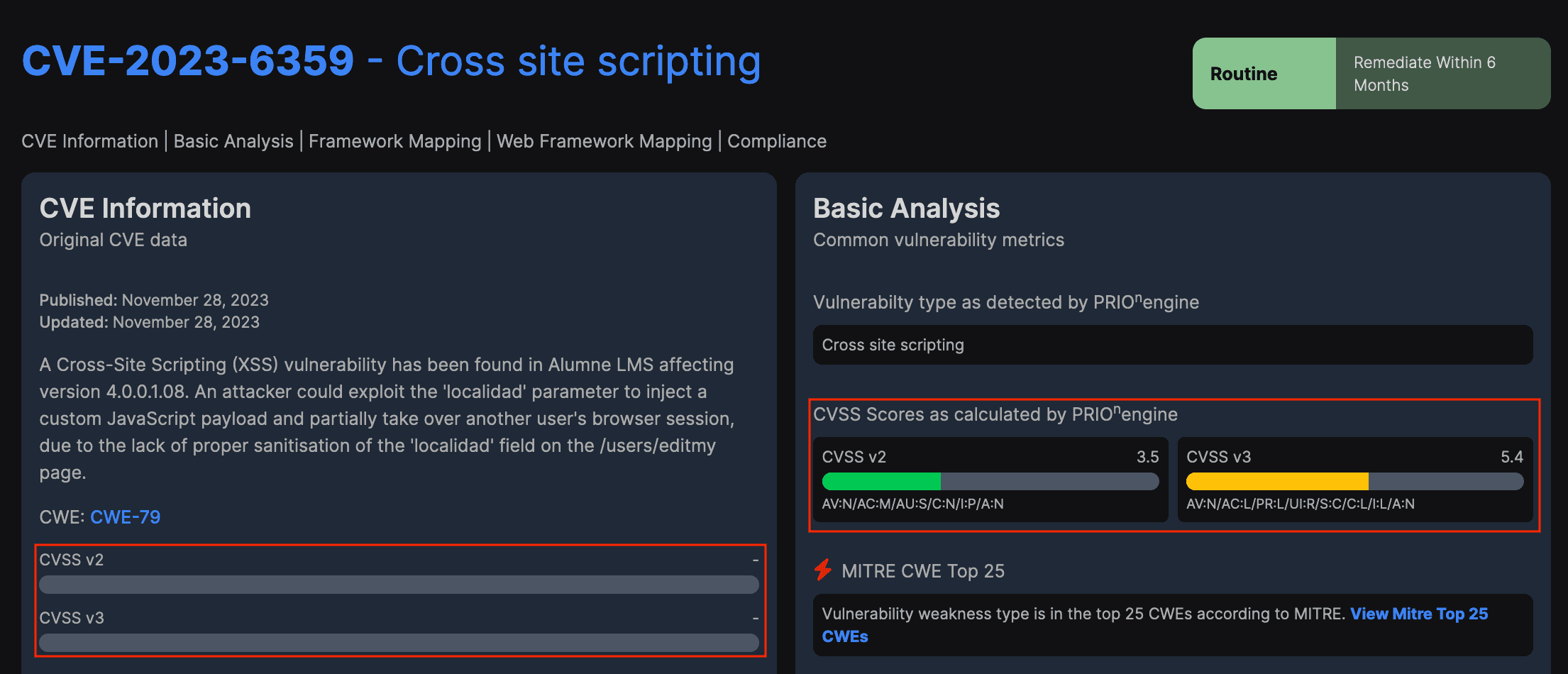
Let's examine the predicted result of the above vulnerability CVE-2023-6459 (Cross-Site Scripting). The vulnerability description as follows:
“A Cross-Site Scripting (XSS) vulnerability has been found in Alumne LMS affecting version 4.0.0.1.08. An attacker could exploit the 'localidad' parameter to inject a custom JavaScript payload and partially take over another user's browser session, due to the lack of proper sanitisation of the 'localidad' field on the /users/editmy page.”
Metric | Value | Description |
Attack Vector | Network | The attack can be exploited over a network. |
Attack Complexity | Low | A malicious actor can exploit this vulnerability at any given opportunity. |
Privileged Required | Low | A malicious actor requires some user level privileges to inject a custom Javascript. |
User Interaction | Required | User Interaction is required for executing the malicious Javascript. |
Status | Changed | The input validation issue is in the Alumne LMS web application, although the malicious Javascript is executed in the victim’s browser. |
Confidentiality | Low | Information in the victim's browser associated with the vulnerable Alumne LMS application can be read by the malicious JavaScript code and sent to the malicious actor. |
Integrity | Low | Information in the victim's browser associated with the vulnerable Alumne LMS application can be modified by the malicious Javascript. |
Availability | None | The malicious JavaScript code cannot impact the victim's browser. |
In the table below, we demonstrate the optimal metrics selected (in bold) by the trained model for CVSSv3 score calculation.
Metric | Score |
AttackVector:Network | 0.9990072846412659 |
AttackVector:Adjacent | 0.00015020475257188082 |
AttackVector:Local | 0.0028139264322817326 |
AttackVector:Physical | 0.0009661060757935047 |
AttackComplexity:Low | 0.9978625178337097 |
AttackComplexity:High | 0.002231457969173789 |
PrivilegeRequired:None | 0.056534409523010254 |
PrivilegeRequired:Low | 0.8863364458084106 |
PrivilegeRequired:High | 0.08969677239656448 |
UserInteraction:None | 0.0007607919978909194 |
UserInteraction:Required | 0.9993075132369995 |
Scope:Unchanged | 0.0025087925605475903 |
Scope:Changed | 0.9971930384635925 |
Confidentiality:None | 0.003172105411067605 |
Confidentiality:Low | 0.9931660294532776 |
Confidentiality:High | 0.014919904060661793 |
Integrity:None | 0.006105166859924793 |
Integrity:Low | 0.9973492622375488 |
Integrity:High | 0.007803104817867279 |
Availability:None | 0.9952024221420288 |
Availability:Low | 0.011401337571442127 |
Availability:High | 0.004767680075019598 |
We can assert that the anticipated CVSSv3 base score of 5.4, along with the vector string CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N, is highly precise.
Case Study: Bug Bounty Report Vulnerability
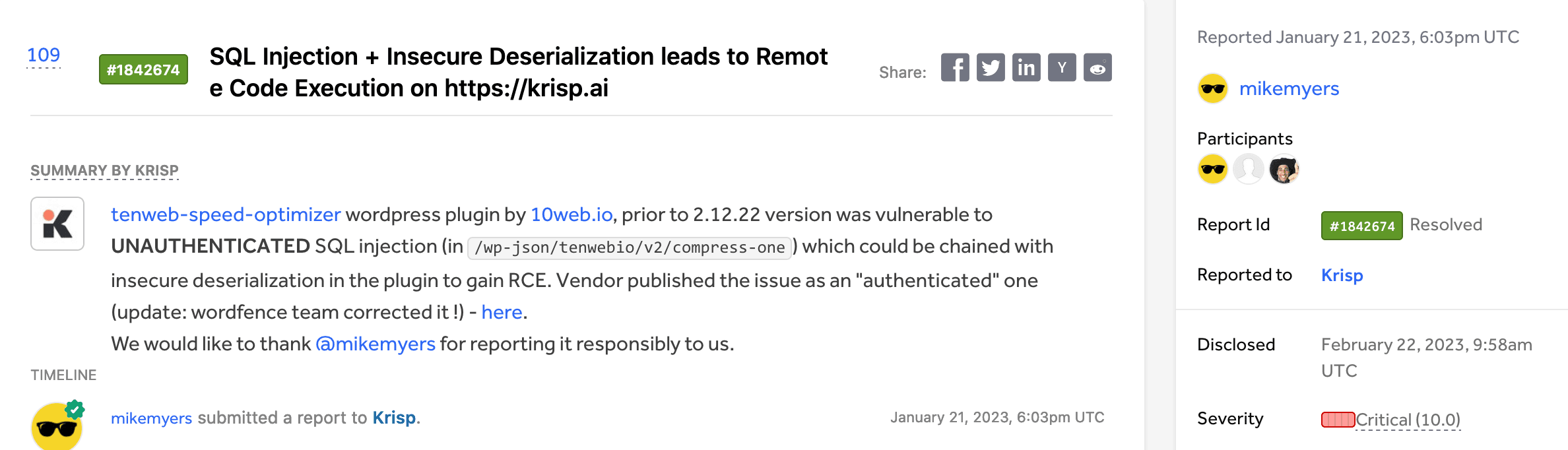
Let's examine the predicted result of the above vulnerability (SQL Injection). The vulnerability description as follows:
“tenweb-speed-optimizer wordpress plugin by 10web.io, prior to 2.12.22 version was vulnerable to UNAUTHENTICATED SQL injection (in /wp-json/tenwebio/v2/compress-one) which could be chained with insecure deserialization in the plugin to gain RCE. Vendor published the issue as an "authenticated" one (update: wordfence team corrected it !)”
Metric | Value | Description |
Attack Vector | Network | The malicious actor can be exploited over a network. |
Attack Complexity | Low | The malicious actor can exploit this vulnerability at any given opportunity. |
Privileged Required | None | A malicious actor requires no privileges to mount an attack. |
User Interaction | None | A malicious actor requires no user interaction to successfully exploit the vulnerability. |
Status | Unchanged | The vulnerable component is a wordpress plugin. No change in scope occurs during the attack. |
Confidentiality | High | In the most severe scenario, a malicious actor can execute remote code, gaining control over both the application and the underlying operating system. |
Integrity | High | In the most severe scenario, a malicious actor can execute remote code, gaining control over both the application and the underlying operating system. |
Availability | High | In the most severe scenario, a malicious actor can shut down the application, or otherwise disrupt service for all users. |
In the table below, we demonstrate the optimal metrics selected (in bold) by the trained model for CVSSv3 score calculation.
Metric | Score |
AttackVector:Network | 0.9982934594154358 |
AttackVector:Adjacent | 0.005101701244711876 |
AttackVector:Local | 0.0008419632213190198 |
AttackVector:Physical | 0.0009174353908747435 |
AttackComplexity:Low | 0.9800256490707397 |
AttackComplexity:High | 0.0214800164103508 |
PrivilegeRequired:None | 0.7126785516738892 |
PrivilegeRequired:Low | 0.3821497857570648 |
PrivilegeRequired:High | 0.010973069816827774 |
UserInteraction:None | 0.9994174242019653 |
UserInteraction:Required | 0.0006388789624907076 |
Scope:Unchanged | 0.9892286062240601 |
Scope:Changed | 0.010386867448687553 |
Confidentiality:None | 0.006437190342694521 |
Confidentiality:Low | 0.02318469248712063 |
Confidentiality:High | 0.9801092147827148 |
Integrity:None | 0.05308257415890694 |
Integrity:Low | 0.01511995866894722 |
Integrity:High | 0.9074390530586243 |
Availability:None | 0.1671636998653412 |
Availability:Low | 0.0021397622767835855 |
Availability:High | 0.8717617988586426 |
We can assert that the anticipated CVSSv3 base score of 9.8, along with the vector string CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H, is highly precise.
Conclusion
A swift and dependable prediction of CVSS base scores for disclosed public or private vulnerabilities is imperative, as highlighted in the 'The Problem' section. Ensuring a prompt and reliable assessment of vulnerabilities is crucial for security professionals to grasp the severity of each vulnerability. At PRIOn, we simplify this process by automatically and transparently generating CVSS vectors and base scores by utilizing the capabilities of our developed Natural Language Processing (NLP) models. PRIOn demonstrates its proficiency in predicting CVSS vectors and base scores for vulnerabilities under scrutiny. As we move forward, we envision PRIOn taking a crucial role in advancing modern vulnerability prioritization practices. This includes furnishing security practitioners with all the essential tools and logic needed for achieving this goal.
How PRIOn can help
PRIOn is an AI driven vulnerability prioritization technology. PRIOn is here to automatically prioritize vulnerabilities, public or private, that matter most across your entire environment. Contact us here for any inquiry/demo. We are here to help you reshape your vulnerability management lifecycle.