In this article we present the analysis of one hundred (100) vulnerabilities that you should keep an eye on and prioritize them according to your environment.
We used PRIOn Knowledge Base for our research. PRIOn Knowledge Base (PRIOn KB) is an online SaaS platform that enables the triaging of publicly disclosed vulnerabilities from the Common Vulnerability Exposure (CVE) program. The main purpose of the PRIOn KB platform is to assist users to analyze, validate and prioritize vulnerabilities.
The scope of this research was to identify, classify and analyze vulnerabilities from the previous year (2022) with the following characteristics:
Vulnerabilities that were zero-day (detected and disclosed to the public)
Vulnerabilities that can be found in the CISA Known Exploited Vulnerabilities (KEV) catalog (CVE-2022-*)
Vulnerabilities that were (are) exploited in the wild
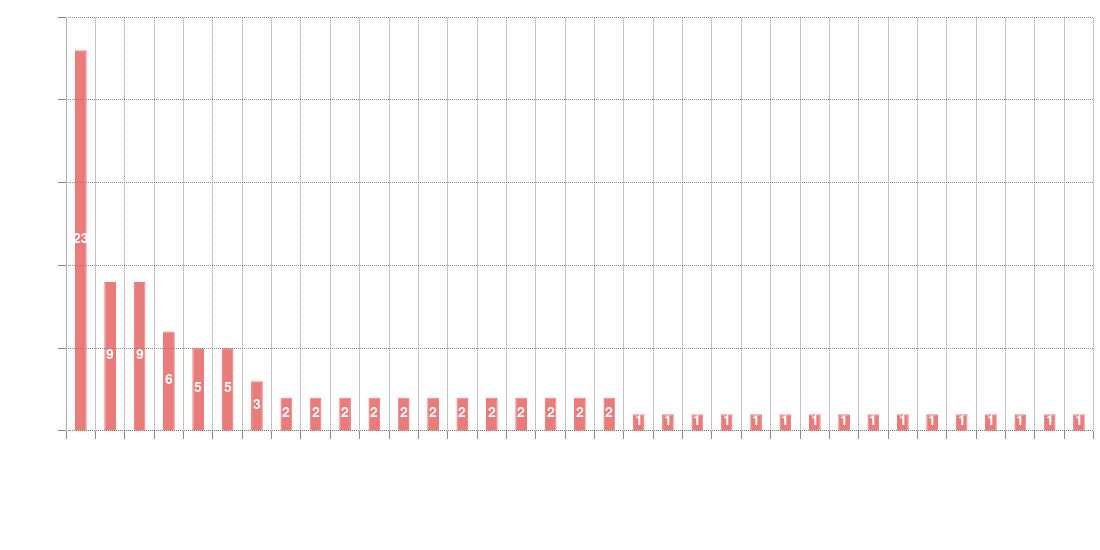
Disclosed vulnerabilities distribution by vendors
During our research we found thirty five (35) vendors/products affected by vulnerabilities with the aforementioned characteristics. The following graph shows that ~23% of the total disclosed vulnerabilities were reported in Microsoft products. The two closest ones were reported in Google and Apple products with ~9% each.
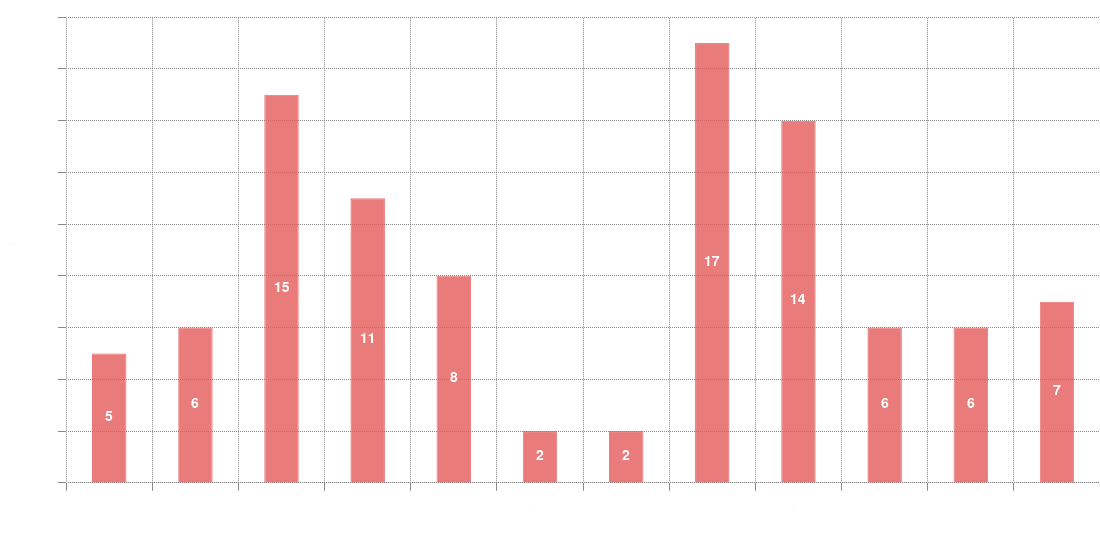
Disclosed vulnerabilities over months
On this graph we can see the disclosed vulnerabilities per month. The most busy months for vulnerabilities seem to be March, April, August and September.
Vulnerability Types
The following graph shows the types of the vulnerabilities under examination. PRIOn core engine extracts the vulnerability types from the CVE description using NLP predictive models. We identified that 33% of the vulnerability types were predicted as Privilege Escalation (~17%) and Remote Code Execution (~16%) respectively.
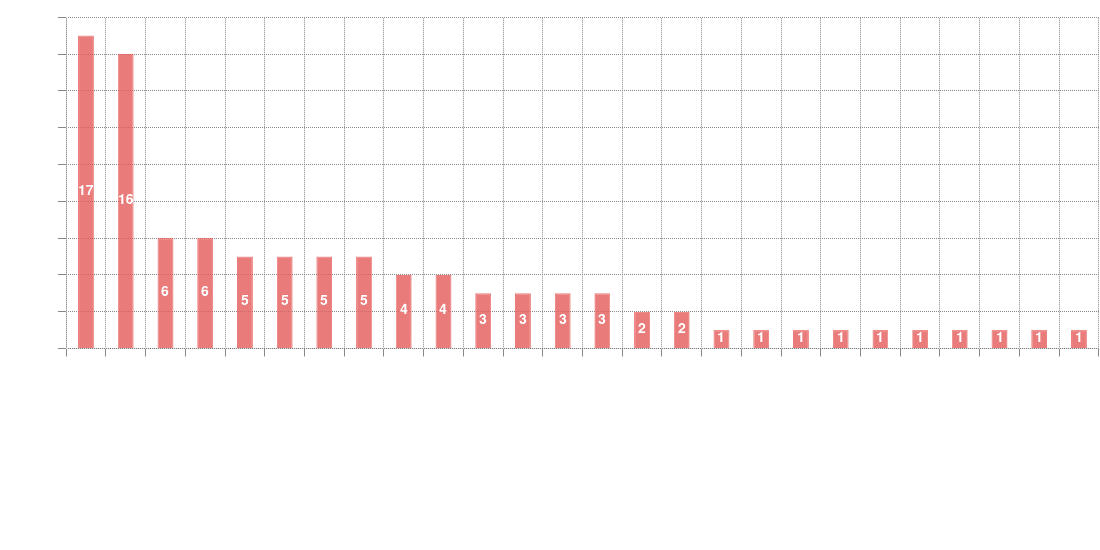
Additionally, many vulnerabilities can be categorized as memory corruption vulnerabilities (super-set), such as Buffer/Heap Overflows, Use Afrer Free, Type confusion etc. In Blackhat (2010) conference a research paper/presentation Memory Corruption Attacks The (almost) Complete History by Thinkst Applied Research, was presented. At that time, memory corruption vulnerabilities monopolized the headlines in the security research community for the past 2 decades, now it’s almost 3 and a half decades. It’s a strong indication that this kind of vulnerabilities, a.k.a memory corruption, will exist for a long time. Other remaining vulnerabilities can be categorized as design or logic flaws including Authentication Bypass, Default Installation etc. Identifying the vulnerability type is very useful in terms of prioritization as not all vulnerability types are equal.
Exploitability
The lowest hanging fruit is exploitability. PRIOn data shows that public exploits (free or paid) can be found, at least, for the half of the vulnerabilities under examination.
During the enrichment and analysis of the vulnerabilities under examination we gathered information about exploit code. The following graph shows the total number of exploits by source.
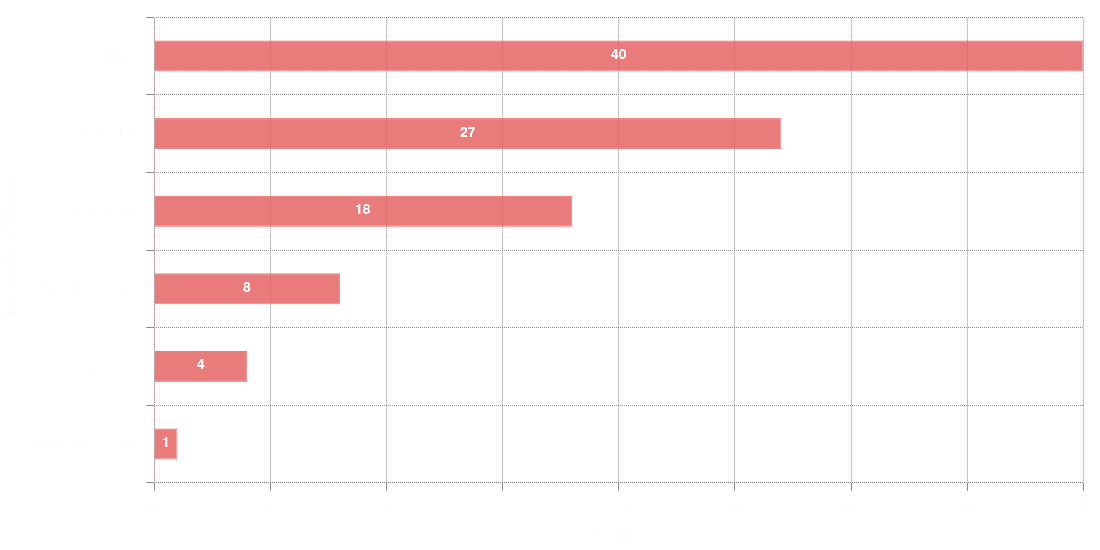
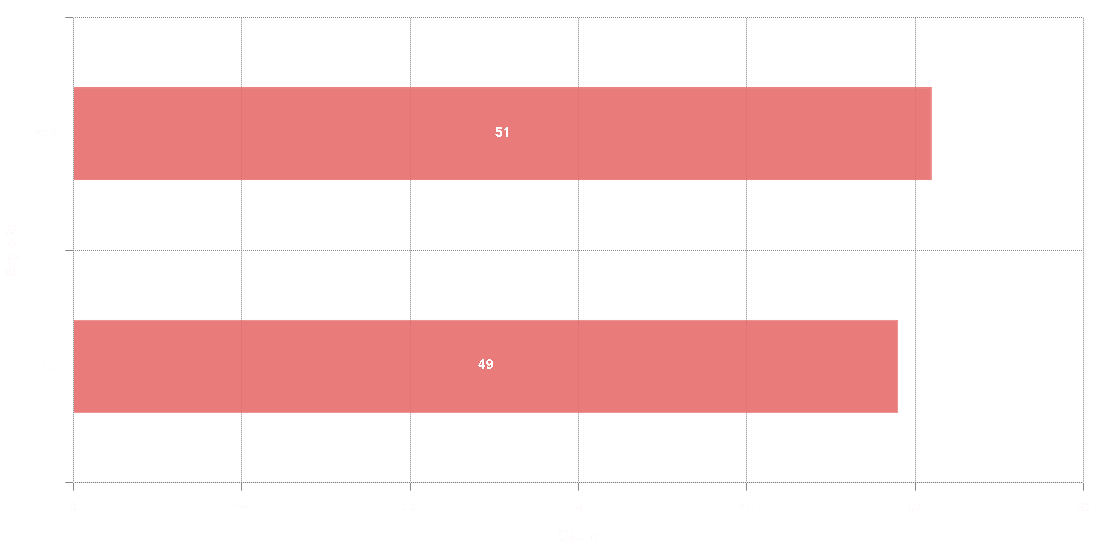
The above graph shows that security researchers are doing their best to disclose exploits to the public. The above graph shows that ~67% of the total exploits were found in various Github repositories and Rapid7 Metasploit® respectively. The exposure of exploitation code to the public could be very helpful for the overall security community, as security researchers are in the position to study various exploitation methods and on top of that to build detection/prevention mechanisms. On the other hand, threat actors, with different motivations, have access to malicious code that it can be exploited to attack infrastructure, applications etc.Addressing vulnerabilities with existing exploit code, either free or paid, should be a high priority for immediate remediation actions. It is very useful to embed this intelligence in your vulnerability management program as you are able to prioritize identified vulnerabilities in a more granular way.
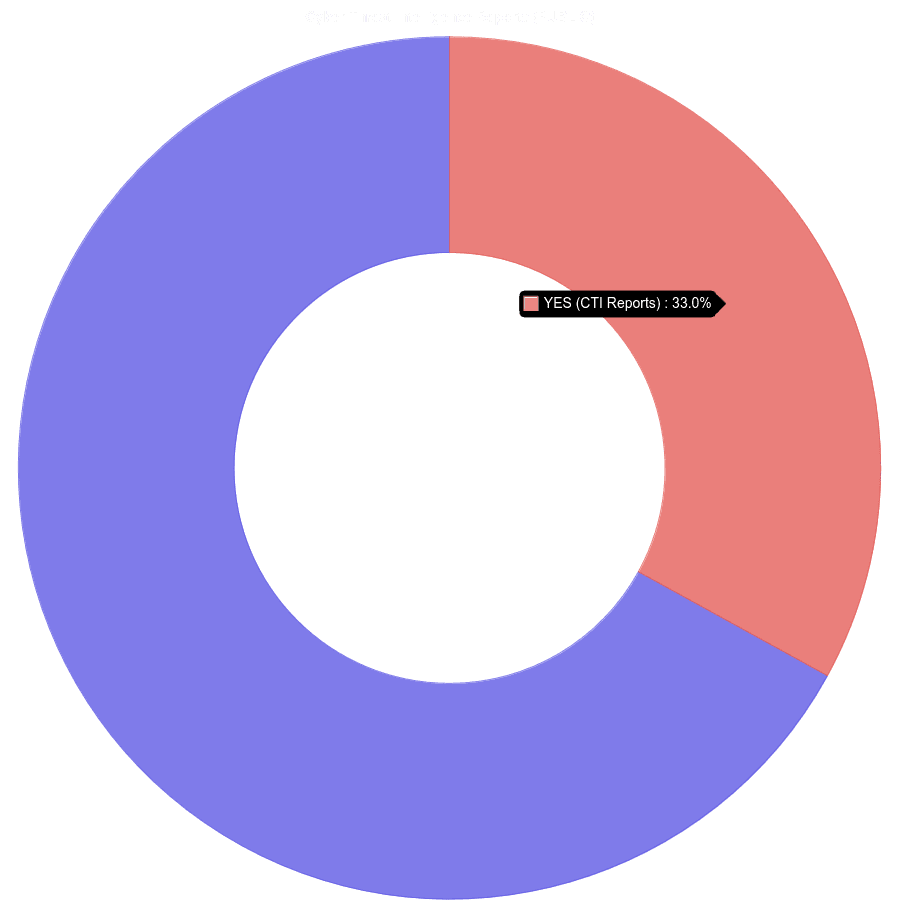
Cyber Threat Intelligence
During our research, we identified that 33% of the total vulnerabilities (100) have been weaponized by threat actors and have been used in hacking activities against various countries and industries. With this kind of information, organizations are able to develop a sense about threat actor groups/vulnerabilities which are relevant to their industries.
The following table contains a list of the affected vendors, the CVE IDs, the threat actors, the potential victim countries and the potentially affected industries.
Vendor | CVE ID | Threat Actors | Victim Countries | Industries |
Microsoft | APT37 (North Korea) | China, Czech, Hong Kong, India, Japan, Kuwait, Nepal, Poland, Romania, Russia, South Korea, UK, USA, Vietnam | Aerospace, Automotive, Chemical, Financial, Government, Healthcare, High-Tech, Manufacturing, Technology, Transportation | |
Microsoft | N/A | Worldwide | Vertical | |
NA | Worldwide | Vertical | ||
Microsoft | Unit 26165 (Russia), SVR (Russia), TA413 (China), APT28 (Russia), UAC-0098 (Russia) | APEC, Afghanistan, Armenia, Australia, Azerbaijan, Belarus, Belgium, Brazil, Bulgaria, Canada, Chechnya, Chile, China, Croatia, Cyprus, Czech, Denmark, Europe, France, Georgia, Germany, Hungary, India, Iran, Iraq, Ireland, Israel, Italy, Japan, Jordan, Kazakhstan, Kyrgyzstan, Latvia, Lebanon, Lithuania, Luxembourg, Malaysia, Mexico, Mongolia, Montenegro, NATO, Netherlands, New Zealand, Norway, OSCE, Pakistan, Palau, Poland, Portugal, Romania, Russia, Singapore, Slovakia, Slovenia, South Africa, South Korea ,Spain, Sweden, Switzerland, Tajikistan, Thailand, Tibet, Turkey, UAE, UK, USA, Uganda, Ukraine, Uzbekistan | Aerospace, Automotive, Aviation, Chemical, Construction, Defense, Education, Embassies, Energy, Engineering, European humanitarian, Financial, Government, Healthcare, IT, Industrial, Intelligence organizations, Law enforcement, Media, NGOs, Non-profit organizations, Oil & gas, Pharmaceutical, Telecommunications, Think Tanks, Transportation | |
Atlassian | SparklingGoblin (China), Lazarus Group (North Korea), DriftingCloud (China) | Argentina, Asia, Europe, Germany, Hong Kong, Iran, Israel, Japan, Kyrgyzstan, Netherlands, Poland, South Africa, USA, Ukraine, Uzbekistan | Aerospace, Blockchain technology companies, Branding and marketing, Critical Infrastructure, Cybersecurity, Defense, Diamond industry, Education, Embassies, Engineering, Financial services, Information Technology, Insurance, Law, Manufacturing, Media, National and local governments, Political entities, Retail, Social services, Telecommunication | |
Microsoft | Tropical Scorpius | Australia, Canada, Colombia, Italy, India, Kuwait, Poland, Taiwan, UAE, USA | Manufacturing, Legal Services, Financial, Construction, Technology, Retail, Real Estate, Government, Transportation, Energy, Education, Healthcare | |
Microsoft | KNOTWEED | Europe, Central America | Vertical | |
Fortinet | APT5 (China) | Europe, Africa, Southeast Asia | Defense, High-Tech, Industrial, Technology, Telecommunication, Government Managed Services | |
Mite | Lorenz | China, Mexico, USA | Enterprises | |
Citrix | APT5 (China) | Southeast Asia | Defense, High-Tech, Industrial, Technology, Telecommunication | |
Zimbra | N/A | Worldwide | Verical | |
VMWare | Donot Team (Russia), Mustang Panda (Russia), Winnti (Russia), TA419 (Russia), Sandworm (Russia), Sednit (Russia), Gamaredon (Russia), InvisiMole (Russia), Turla (Russia), Buhtrap (Russia) | Worldwide | Vertical | |
Google Chrome | Candiru | Middle East, Lebanon | Journalists | |
Sophos | TA413 (China), DriftingCloud (China) | Tibet, Europe, WorldWide | Religious, Vertical | |
Zimbra | N/A | Central Asia | Vertical | |
Zimbra | N/A | Worldwide | Vertical | |
Zimbra | N/A | Worldwide | Vertical | |
RARLAB | N/A | Worldwide | Vertical | |
Apache | N/A | Worldwide | Vertical | |
VMWare | Various | Worldwide | Multiple large organizations | |
VMWare | Killnet (Russia) | Czech Republic, Ukraine, NATO | Airports, Government | |
F5 | Various (China) | USA | Information Technology, Telecommunications, Defense Industrial Base, Critical Infrastructure | |
Microsoft | BlueSky | Worldwide | Verical | |
Zyxel | Europe, North America, South America, Asia Pacific | Enterprises, Consumer Services | ||
WSO2 | N/A (China) | Worldwide | Vertical | |
DLink | N/A | Worldwide | Vertical | |
DOTCMS | H0lyGh0st | Worldwide | Schools, Banks, Mid-Sized Businesses | |
DLink | N/A | Worldwide | Vertical | |
Watchguard | Sandworm | Azerbaijan, Belarus, France, Georgia, Iran, Israel, Kazakhstan, Kyrgyzstan, Lithuania, Poland, Russia, Ukraine | Education, Energy, Government, Telecommunications | |
Spring Cloud | N/A | Worldwide | Vertical | |
Spring Cloud | N/A | Worldwide | Vertical | |
Debian (Redis) | N/A | Worldwide | Vertical | |
Zimbra | N/A | Worldwide | Vertical |
Taxonomies
PRIOn ML predictive models map certain cyber security taxonomies, such as MITRE taxonomies, with CVEs. Under the following sections, we present our analysis for MITRE CAPEC™ and MITRE ATT&CK®. Both taxonomies describe threat actor behaviors. CAPEC™ describes the exploitation of a software vulnerability and provides information on how to secure a software vulnerability. On the other hand, MITRE ATT&CK® describes the behavior of adversaries TTPs in different attack stages with focus on how to mitigate and detect those behaviors. Attack patterns provided by CAPEC™ can be a part of MITRE ATT&CK® techniques or sub-techniques. Both taxonomies can assist defenders with the prioritization of the identified vulnerabilities in their environment.
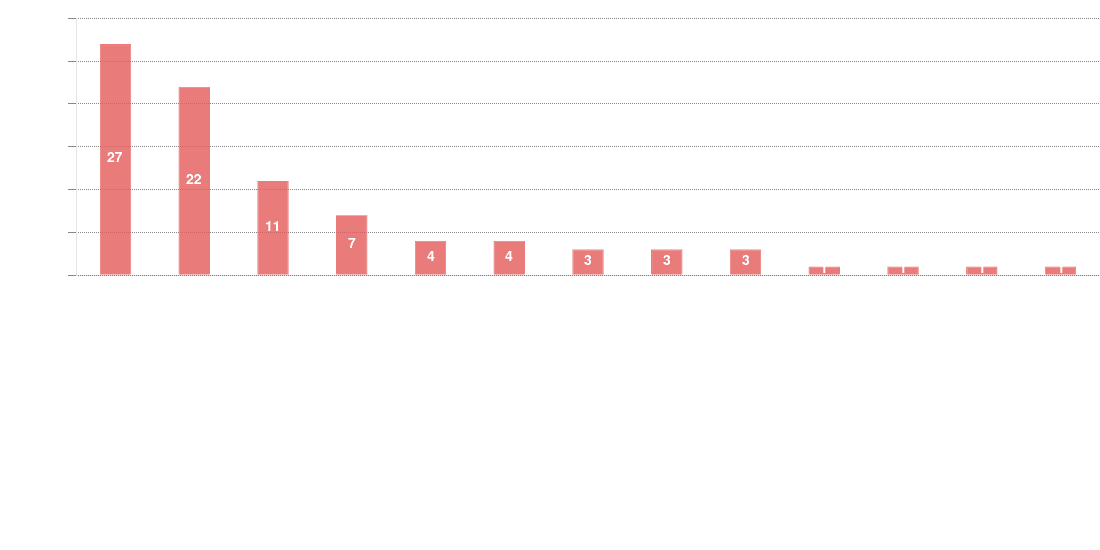
Common Attack Pattern Enumerations and Classifications (CAPEC™)
PRIOn ML predictive models map CVEs to relevant CAPEC known attack patterns. A CAPEC attack pattern is a description, in an abstract way, of a common software exploitation method, for instance Code Injection or SQL Injection. The following graph shows that the 70% of the identified known attack patterns predicted as Code Injection (CAPEC-242), Privilege Escalation (CAPEC-233) and OS Command Injection (CAPEC-88) respectively.
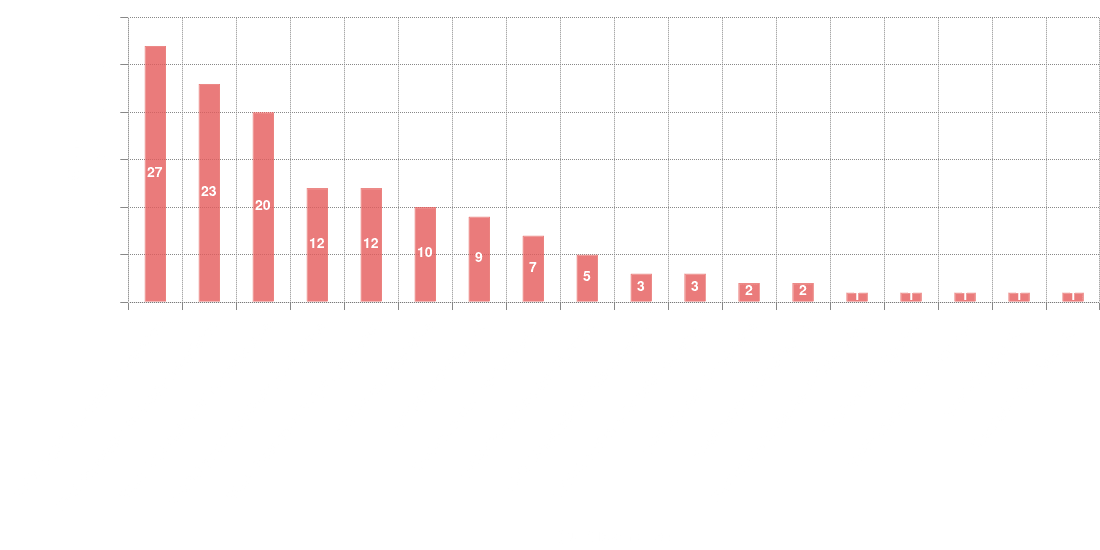
MITRE ATT&CK®
PRIOn ML predictive models map CVEs to relevant techniques from the MITRE ATT&CK® matrix. The following graph shows all the techniques that were mapped, automatically, during this research. The 50% of the total count of MITRE ATT&CK® techniques were predicted and mapped as T1203-Exploitation for client execution, T1068-Exploitation for privilege escalation and T1210-Exploitation for remote services respectively.
By linking and mapping MITRE ATT&CK® techniques to CVEs, PRIOn engine provides risk insights to defenders. The defender can understand in which attack stage (e.g. cyber kill chain) the adversary may use the vulnerability and plan accordingly. Information can be used to: deploy and test defense control capabilities for prevention purposes, create threat hunting scenarios for daily threat hunting activities, enrich internal threat intelligence and knowledge base or to simulate adversary exercises. Finally, defenders can group techniques (by tactics) to prioritize vulnerabilities relevant to their environment.
Reconnaissance | Resource Development | Initial Access | Execution | Persistence | Privilege Escalation | Defense Evasion | Credential Access | Discovery | Lateral Movement | Collection | Command and Control | Exfiltration | Impact |
T1589 - Gather Victim Identity Information | T1608 - Stage Capabilities | T1190-Exploit Public Facing Application T1133-External Remote Services | T1203-Exploitation for Client Execution T1059-Command & Scripting Interpreter T1204.001-Malicious Link | T1133-External Remote Services | T1068-Exploitation for Privilege Escalation | T1497-Virtualization/Sandbox Evasion T1221-Template Injection T1036-Masquarading T1027.006-HTML Smuggling | T1552-Unsecured Credentials | T1083-File and Directory Discovery T1497-Virtualization/Sandbox Evasion | T1210-Exploitation for Remote Services | T1499-Endpoint Denial of Serices |
Vulnerable Products
In the following sections we describe the vulnerabilities per vendor/product. Each table contains the following information:
Vendor/Product
CVE ID
Disclosed Month
Vulnerability Type
PRIOn Score
Score (Number, color)
Tooltip Indicators (Zero Day, Exploits, Exploited in the wild, CTI)
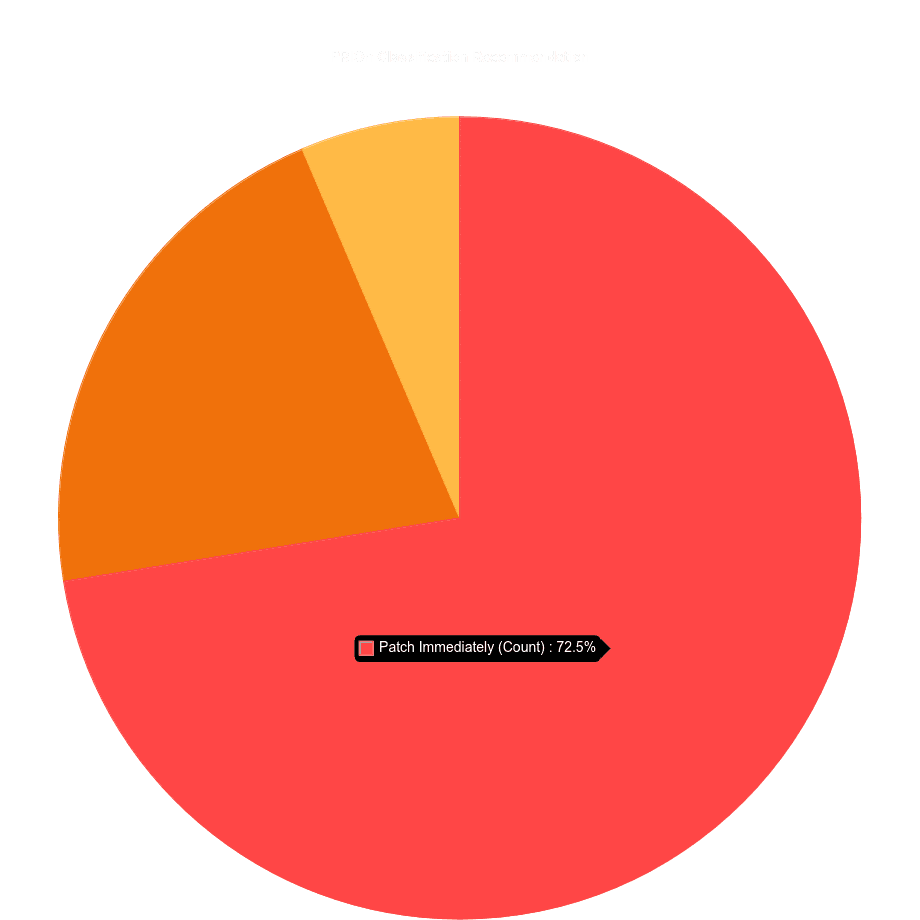
The following pie chart shows the PRIOn Classification Recommendation for the vulnerabilities under examination. More than 70% of the total vulnerabilities could be classified as Patched Immediately, more than 20% could be classified as Must be Patched and less than 7% could be classified as Should be Patched.
Microsoft Product
The following table shows the vulnerabilities affecting Microsoft products.
Product | CVE ID | Disclosed Month | Vulnerability Type | PRIOn Score |
Windows (Microsoft Windows Support Diagnostic Tool (MSDT)) | May | Remote Code Execution | 98 | |
Windows (Win32k.sys driver) | January | Privilege Escalation | 98 | |
Windows (Windows Scripting Languages (JScript9)) | November | Remote Code Execution | 94 | |
Microsoft Exchange Server | September | Remote Code Execution | 94 | |
Microsoft Exchange Server | September | Remote Code Execution | 94 | |
Windows (Windows Common Log File System Driver) | April | Privilege Escalation | 94 | |
Windows (Windows CSRSS) | July | Privilege Escalation | 94 | |
Windows (Windows CNG Key Isolation Service) | November | Privilege Escalation | 86 | |
Windows (Windows COM+ Event System Service) | October | Privilege Escalation | 86 | |
Windows (Windows LSA Spoofing) | May | Spoofing | 86 | |
Windows (Windows Common Log File System Driver) | September | Privilege Escalation | 86 | |
Microsoft Exchange Server | January | Privilege Escalation | 86 | |
Windows (Active Directory Domain Services) | August | Privilege Escalation | 86 | |
Windows (Windows Print Spooler) | April | Privilege Escalation | 86 | |
Windows (Windows Print Spooler) | March | Privilege Escalation | 86 | |
Windows (Windows Runtime) | August | Privilege Escalation | 86 | |
Windows (Windows SmartScreen ) | December | Security Feature Bypass | 85 | |
Windows (Mark of the Web) | November | Security Feature Bypass | 85 | |
Windows (Mark of the Web) | November | Security Feature Bypass | 85 | |
Windows (Windows Print Spooler) | November | Privilege Escalation | 84 | |
Windows (Windows User Profile Service) | April | Privilege Escalation | 84 | |
Windows (Windows Support Diagnostic Tool (MSDT)) | August | Remote Code Execution | 71 | |
Windows (Windows User Profile Service) | April | Privilege Escalation | 71 |
Google Products
The following table shows the vulnerabilities affecting Google products.
Product | CVE ID | Disclosed Month | Vulnerability Type | PRIOn Score |
Chrome (WebRTC) | August | Heap Overflow | 94 | |
Chrome (Mojo) | September | Input Validation | 88 | |
Chrome (V8 JavaScript engine ) | December | Type Confusion | 86 | |
Chrome (V8) | October | Type Confusion | 86 | |
Chrome (V8 Turbofan) | May | Type Confusion | 86 | |
Chrome (V8) | March | Type Confusion | 86 | |
Chrome (Animation) | February | Use After Free | 86 | |
Chrome (Intents) | August | Input Validation | 85 | |
Chrome (GPU) | November | Heap Overflow | 84 |
Apple Products
The following table shows the vulnerabilities affecting Apple products.
Product | CVE ID | DIsclosed Month | Vulnerability Type | PRIOn Score |
Safari/tvOS/macOS/iPadOS/iOS | December | Type Confusion | 86 | |
iOS/iPadOS | October | Out Of Bounds | 86 | |
MacOS/iOS/iPadOS | September | Remote Code Execution | 86 | |
iOS/iPadOS/MacOS | August | Out Of Bounds | 86 | |
IOS/iPadOS/MacOS/Safari | August | Out Of Bounds | 86 | |
tvOS/watchOS/macOS/iOS/iPadOS | March | Out Of Bounds | 86 | |
MacOS/iOS/iPadOS/Safari | February | Use After Free | 86 | |
MacOS | April | Out Of Bounds | 85 | |
IOS/iPadOS/MacOS | January | Memory Corruption | 75 |
Cisco Products
The following table shows the vulnerabilities affecting CISCO products.
Product | CVE ID | Disclosed Month | Vulnerability Type | PRIOn Score |
Small Business | March | Buffer Overflow | 88 | |
IOS XR Software | May | Input Validation | 85 | |
Small Business | March | Buffer Overflow | 75 | |
Small Business | March | Buffer Overflow | 75 | |
Small Business | March | Buffer Overflow | 75 | |
Small Business | March | Buffer Overflow | 75 |
Zimbra Products
The following table shows the vulnerabilities affecting Zimbra products.
Product | CVE ID | Disclosed Month | Vulenrability Type | PRIOn Score |
Collaboration | August | Directory Traversal | 96 | |
Collaboration | October | Unrestricted File Upload | 95 | |
Collaboration | August | Unrestricted File Upload | 95 | |
Collaboration | February | Cross Site Scripting | 94 | |
Collaboration | August | Command Injection | 80 |
VMware Products
The following table shows the vulnerabilities affecting VMWare products.
Product | CVE ID | Disclosed Month | Vulnerability Type | PRIOn Score |
Workspace ONE Access/Identity Manager | April | Remote Code Execution | 96 | |
Spring WebFlux | April | Remote Code Execution | 95 | |
Spring Cloud | August | Remote Code Execution | 95 | |
Spring Cloud Gateway | May | Remote Code Execution | ||
Workspace ONE Access/Identity Manager/vRealize Automation | April | Privilege Escalation | 94 |
Atlassian Products
The following table shows the vulnerabilities affecting Atlassian products.
Product | CVE ID | Disclosed Month | Vulnerability Type | PRIOn Score |
Confluence/Data Center | May | Remote Code Execution | 95 | |
Questions For Confluence | July | Hardcoded Credentials | 88 | |
BitBucket | September | Command Injection | 86 |
Remaining Vendors/Products
The following table shows the vulnerabilities of the remaining affected vendors products.
Vendor | Product | CVE ID | Disclosed Month | Vulnerability Type | PRIOn Score |
Fortinet | SSL-VPN | December | Heap Overflow | 99 | |
F5 | BigIP | May | Authentication | 99 | |
Zyxel | USG Flex | May | Command Injection | 99 | |
Apache | APISIX | August | Authentication | 96 | |
dotCMS | dotcms | August | Directory Traversal | 96 | |
Mitel | Mivoice Connect | June | Input Validation | 95 | |
Citrix | Gateway, ADC | December | Remote Code Execution | 95 | |
Sophos | Firewall | Authentication | 95 | ||
RARLAB | Unrar | August | Directory Traversal | 95 | |
WSO2 | API manager/Enterprise | April | Unrestricted File Upload | 95 | |
Debian | Redis | March | Sandbox Bypass | 93 | |
CWP | WebPanel | January | Command Injection | 92 | |
Fortinet | FortiOS, FortiProxy, FortiSwitchManager | October | Authentication | 89 | |
QNAP | Photo Station | September | Externally Controlled Reference | 88 | |
TrendMicro | Apex Central | March | Unrestricted File Upload | 88 | |
Sophos | User Portal/Webadmin | September | Code Injection | 88 | |
Mozilla | Firefox | March | Use After Free | 88 | |
Adobe | Magento Commerce | February | Input Validation | 88 | |
Zoho | ManageEngine | Remote Code Execution | 88 | ||
Veeam | Backup & Replication | December | Improper Access Control | 88 | |
Veeam | Backup & Replication | December | Remote Code Execution | 88 | |
Watchguard | Fireware | March | Authentication | 88 | |
Apache | CouchDB | August | Default Installation | 88 | |
SAP | NetWeaver, ABAP, Dispatcher, Content | August | Request Smuggling | 88 | |
Zoho | Manage Engine | January | Remote Code Execution | 87 | |
TrendMicro | Apex One | September | Input Validation | 86 | |
Mozilla | FIrefox | March | Use After Free | 86 | |
Linux | Flags | April | Privilege Escalation | 86 | |
Shift Tech Inc. | Bingo!CMS | October | Authentication | 83 | |
D-Link | DIR816L Firmware | September | Remote Code Execution | 82 | |
D-Link | DIR-820L Firmware | September | Command Injection | 82 | |
WatchGuard | Firewall | April | Privilege Escalation | 78 | |
Mitel | MiCollab | Improper Access Control | 75 | ||
WordPress | BackupBuddy | September | Authorization | 73 | |
Palo Alto Networks | PanOS, Prisma, Cloud NGFW | August | Denial of Service | 71 | |
Wordpress | WPGateway | September | Authorization | 71 | |
Linux Kernel | Flags | N/A | Double Free | 69 | |
Zabbix | Frontend | February | Improper Access Control | 68 Exploited in the wild | |
Owl Labs | Meeting Owl | June | Hardcoded Credentials | 66 |
Conclusion
In this blog we presented our security research and analysis of one hundred (100) vulnerabilities for the year 2022. Our analysis was done via the PRIOn Knowledge Base platform. It is clear that security researchers are doing their best to provide information to the public related to vulnerabilities (zero day or known exploited) exploited in the wild. PRIOn Knowledge Base, collects, enriches and analyses publicly disclosed vulnerabilities from the CVE program. It provides actionable data to cyber security practitioners to ensure that the most severe and dangerous vulnerabilities are prioritized. Each vulnerability is assigned a risk score according to its unique characteristics.
If you have any questions/comments/suggestions/corrections regarding our analysis, feel free to contact us.