What is Patch Tuesday
Patch Tuesday refers to regular, scheduled releases of software patches and updates by various technology companies, including Microsoft, Adobe, Oracle etc. It occurs on the second Tuesday of each month. During Patch Tuesday, Microsoft releases:
Security Updates
Bug Fixes
Improvements in its products (Windows OS, MS Office, other supported MS applications)
February 2024
Microsoft has rolled out security patches covering 74 vulnerabilities, with two of these are currently under active exploitation. These (2) vulnerabilities can be found in the CISA Known Exploited Vulnerability (KEV) catalog.
CVE-2024-21412 (0day - Security Feature Bypass): Internet Shortcut Files Security Feature Bypass Vulnerability.
CVE-2024-21351 (0day - Security Feature Bypass): Windows SmartScreen Security Feature Bypass Vulnerability.
CVE-2024-21410 (0day - Privilege Escalation): Microsoft Exchange Server Elevation of Privilege Vulnerability.
Products
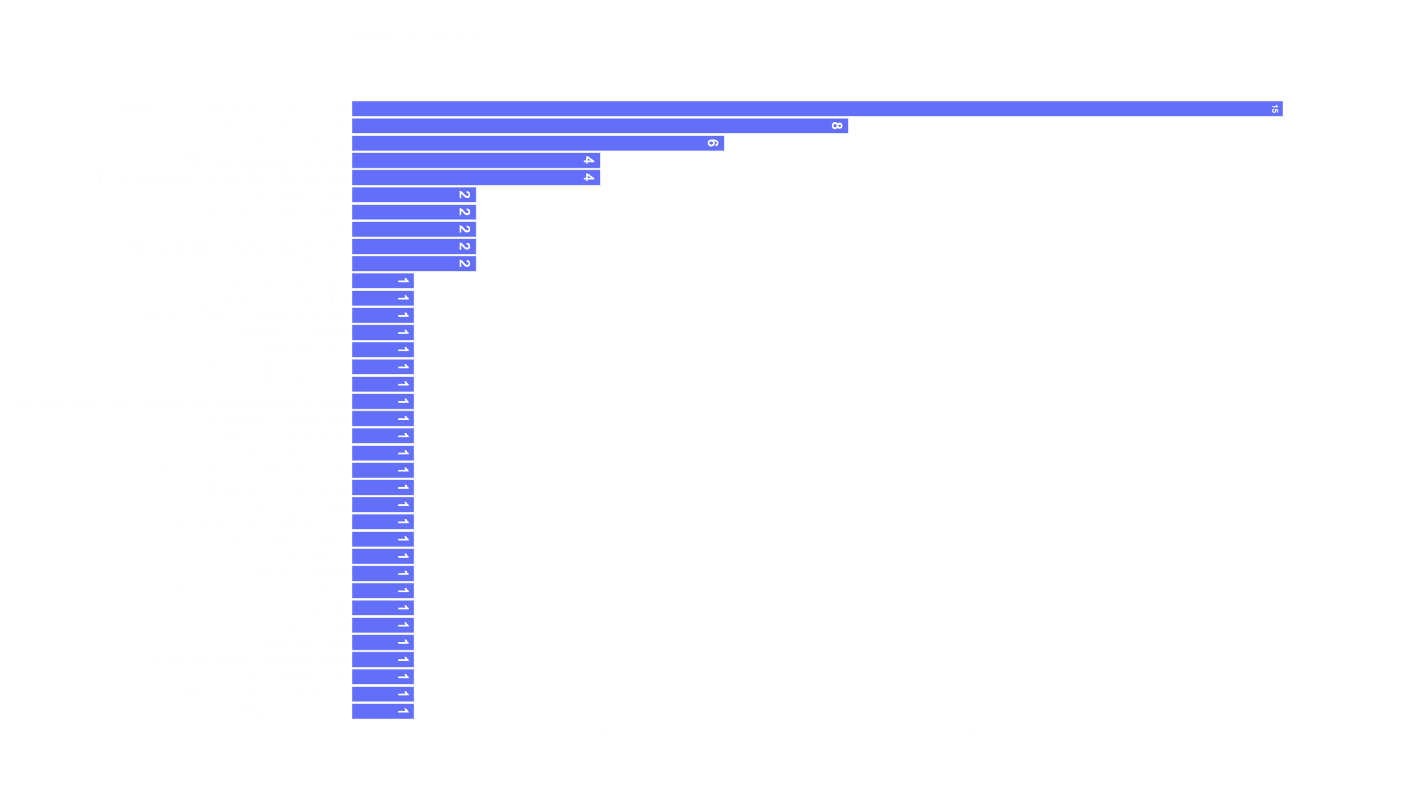
In the provided image below, we can see that the primary vulnerable products are Microsoft WDAC OLE DB provider for SQL, followed by Microsoft Dynamics and Windows Kernel.
Vulnerability Types
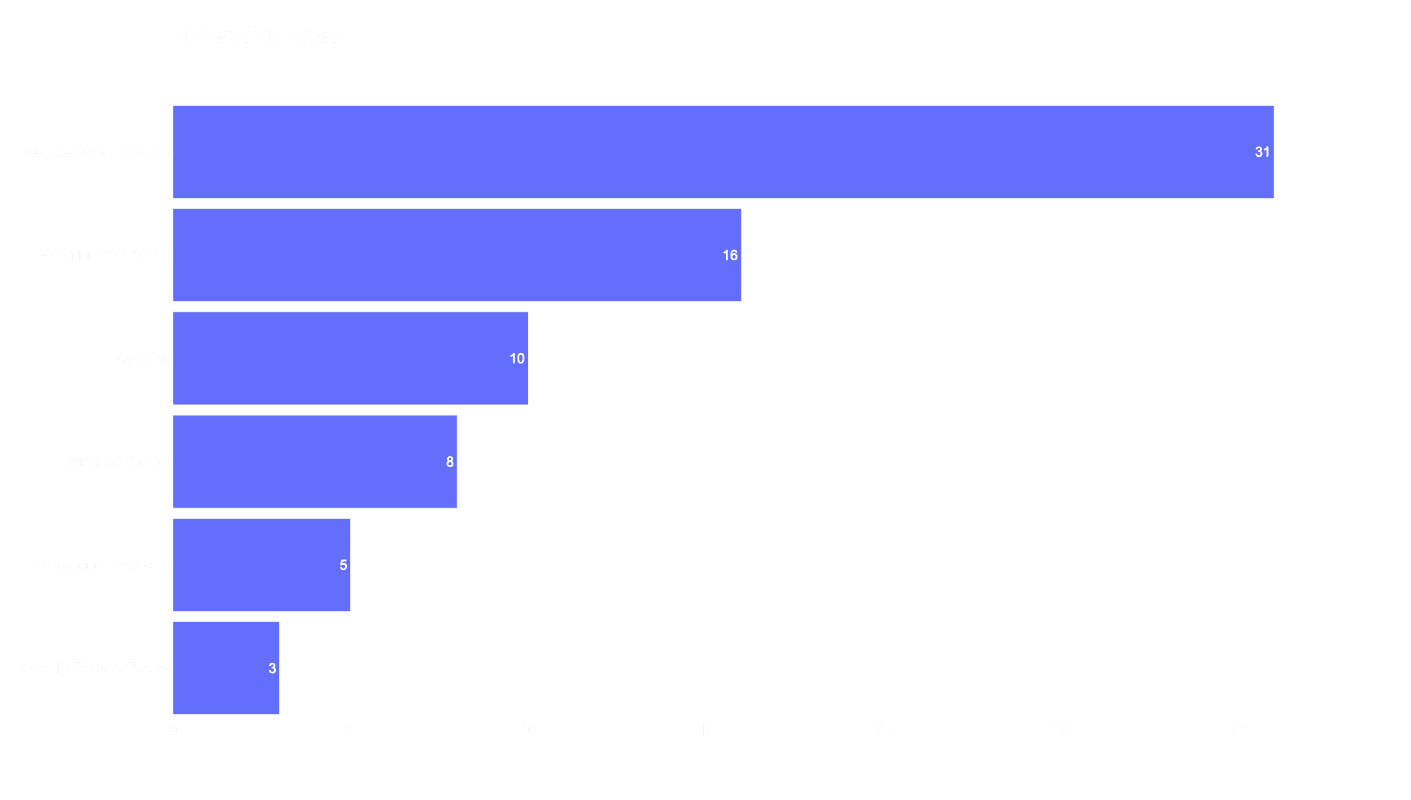
In the image below we can observe that the predominant vulnerability type for this month is Remote Code Execution (31), trailed by Elevation of Privilege (16) and spoofing (10) respectively.
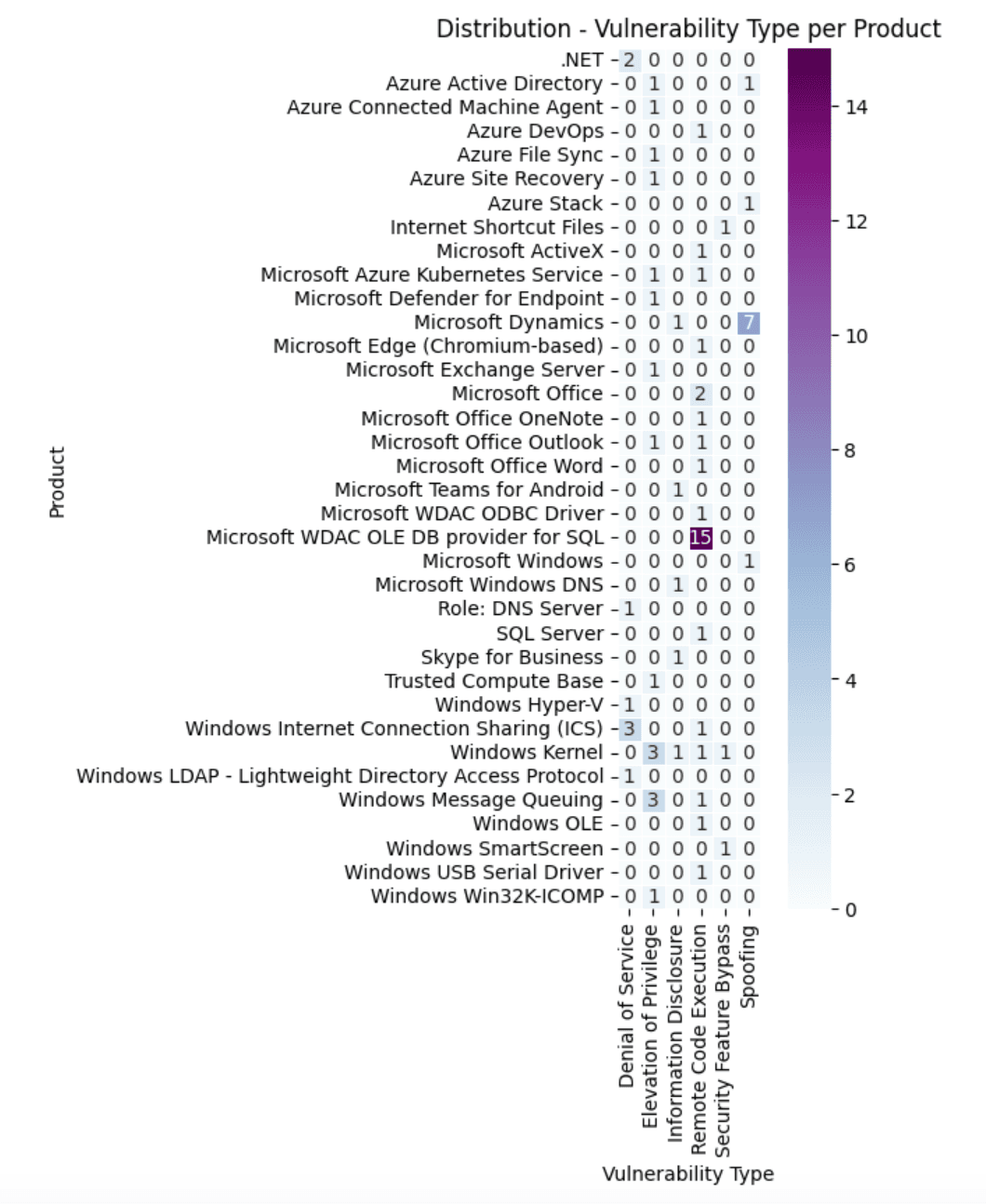
The below heatmap depicts the distribution of various vulnerability types per MS product.
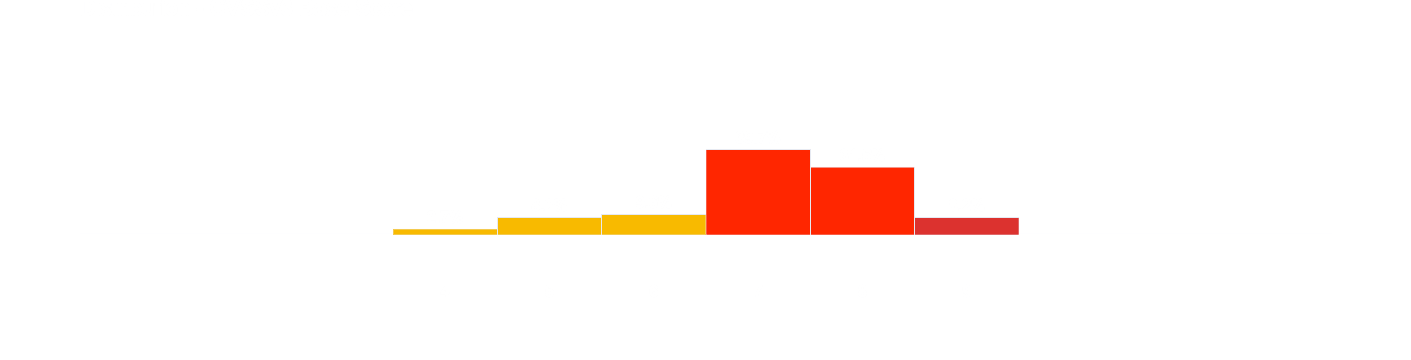
CVSSv3 Score Distribution
It becomes evident that a significant majority of vulnerabilities gravitates towards the range of 7 to 9. This cluster underscores the high to critical severity of these vulnerabilities.
Some statistics about CVSSv3 score distribution:
mean: ~7.7
min: 4.1
max: 9.8
25%: 7.1
50%: 7.8
75%: 8.8
median: 7.8
PRIOn KB Prioritization Decision Engine
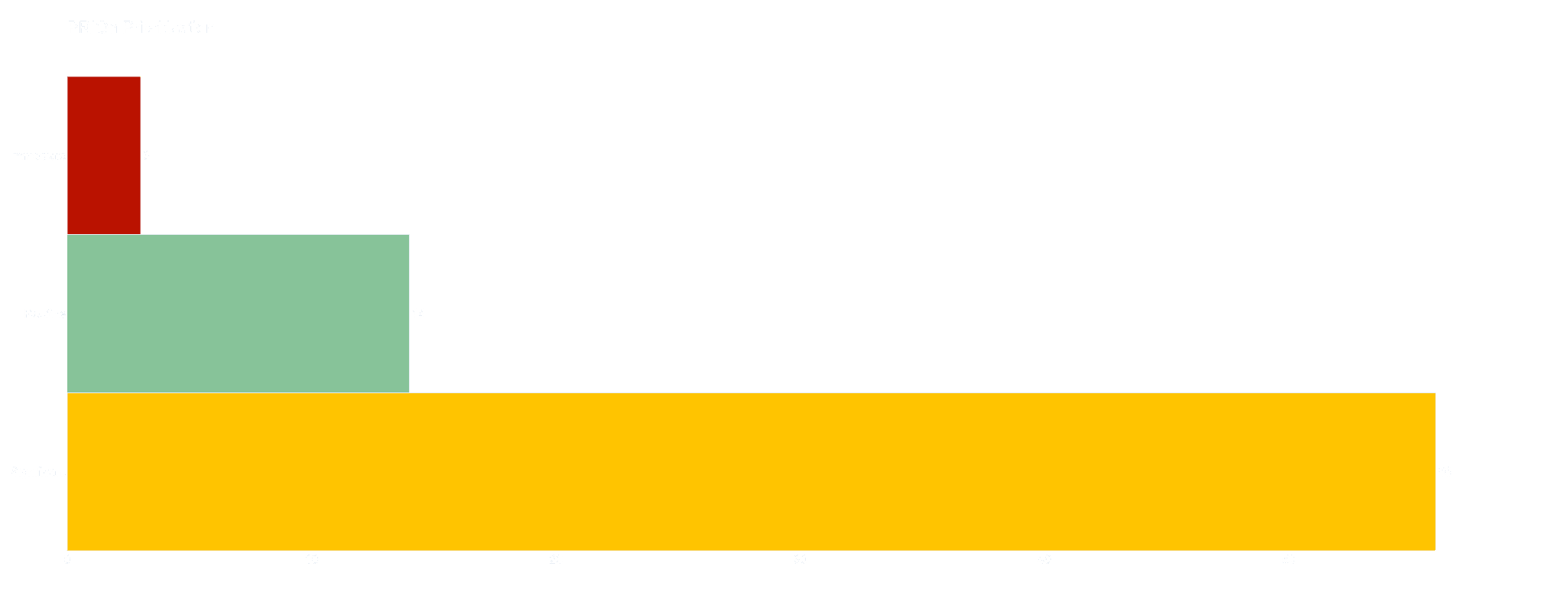
PRIOn KB prioritization decision engine provides sensible default prioritization for vulnerabilities, which can also be customized to align with your security policies and requirements. The below horizontal bar chart provides a visual presentation of the distribution of vulnerabilities analysed via the PRIOn KB decision engine. At a glance, it becomes evident that the majority of the vulnerabilities, comprising a substantial 76.7% of the total, fail into the “Significant” risk priority level. The “Routine” priority level makes up 19.2% of the chart. This Significant priority level represents vulnerabilities that demand a higher level of attention than the “Routine” risk level vulnerabilities but are not yet classified as “Urgent” or “Immediate" risk. The “Immediate” risk level category, while the smallest at 4.1%, emphasizes vulnerabilities that demand the highest priority remediation effort.
In the table below, we have arranged all the examined CVEs by priority.
CVE | Score | Priority Label |
|---|---|---|
CVE-2024-21412 | 94 | Immediate |
CVE-2024-21410 | 88 | Immediate |
CVE-2024-21351 | 86 | Immediate |
CVE-2024-21413 | 68 | Significant |
CVE-2024-21401 | 68 | Significant |
CVE-2024-21403 | 66 | Significant |
CVE-2024-21376 | 66 | Significant |
CVE-2024-21364 | 66 | Significant |
CVE-2024-21342 | 63 | Significant |
CVE-2024-21395 | 62 | Significant |
CVE-2024-21393 | 62 | Significant |
CVE-2024-21389 | 62 | Significant |
CVE-2024-21327 | 62 | Significant |
CVE-2024-21420 | 61 | Significant |
CVE-2024-21406 | 61 | Significant |
CVE-2024-21405 | 61 | Significant |
CVE-2024-21404 | 61 | Significant |
CVE-2024-21402 | 61 | Significant |
CVE-2024-21399 | 61 | Significant |
CVE-2024-21396 | 61 | Significant |
CVE-2024-21394 | 61 | Significant |
CVE-2024-21391 | 61 | Significant |
CVE-2024-21386 | 61 | Significant |
CVE-2024-21384 | 61 | Significant |
CVE-2024-21380 | 61 | Significant |
CVE-2024-21379 | 61 | Significant |
CVE-2024-21378 | 61 | Significant |
CVE-2024-21377 | 61 | Significant |
CVE-2024-21375 | 61 | Significant |
CVE-2024-21372 | 61 | Significant |
CVE-2024-21371 | 61 | Significant |
CVE-2024-21370 | 61 | Significant |
CVE-2024-21369 | 61 | Significant |
CVE-2024-21368 | 61 | Significant |
CVE-2024-21367 | 61 | Significant |
CVE-2024-21366 | 61 | Significant |
CVE-2024-21365 | 61 | Significant |
CVE-2024-21363 | 61 | Significant |
CVE-2024-21361 | 61 | Significant |
CVE-2024-21360 | 61 | Significant |
CVE-2024-21359 | 61 | Significant |
CVE-2024-21358 | 61 | Significant |
CVE-2024-21357 | 61 | Significant |
CVE-2024-21355 | 61 | Significant |
CVE-2024-21354 | 61 | Significant |
CVE-2024-21353 | 61 | Significant |
CVE-2024-21352 | 61 | Significant |
CVE-2024-21350 | 61 | Significant |
CVE-2024-21349 | 61 | Significant |
CVE-2024-21348 | 61 | Significant |
CVE-2024-21347 | 61 | Significant |
CVE-2024-21346 | 61 | Significant |
CVE-2024-21345 | 61 | Significant |
CVE-2024-21338 | 61 | Significant |
CVE-2024-21329 | 61 | Significant |
CVE-2024-21328 | 61 | Significant |
CVE-2024-21315 | 61 | Significant |
CVE-2024-20673 | 61 | Significant |
CVE-2024-20667 | 61 | Significant |
CVE-2024-21397 | 59 | Routine |
CVE-2024-21381 | 59 | Routine |
CVE-2024-21374 | 59 | Routine |
CVE-2024-21362 | 59 | Routine |
CVE-2024-21356 | 59 | Routine |
CVE-2024-21344 | 59 | Routine |
CVE-2024-21343 | 59 | Routine |
CVE-2024-21341 | 59 | Routine |
CVE-2024-21340 | 59 | Routine |
CVE-2024-21339 | 59 | Routine |
CVE-2024-21304 | 59 | Routine |
CVE-2024-20695 | 59 | Routine |
CVE-2024-20684 | 59 | Routine |
CVE-2024-20679 | 59 | Routine |
How PRIOn can help
PRIOn is an AI driven vulnerability prioritization technology. PRIOn is here to automatically prioritize vulnerabilities, public or private, that matter most across your entire environment. Contact us here for any inquiry/demo. We are here to assist you to transform your vulnerability management lifecycle.