Highlights
CVE-2023-23397 seems to be one of the most dangerous vulnerability in Q1 2023 as no user interaction is needed. It is a Privilege Escalation vulnerability and affects all versions of Microsoft Outlook desktop. APT28 threat actor group took advantage of this vulnerability to attack sectors such as Governments, Military, Energy and Transportation in broader Europe. A Bypass Authentication vulnerability,
CVE-2023-27350 affected Papercut servers. Bl00dy, Clop and Lockbit ransomware operations took advantage of this vulnerability by attacking different countries and sectors to steal corporate data.
Mirai Botnet, and variations of it , took advantage of two critical CVE vulnerabilities, the
CVE-2023-28771 (Zyxel) and the CVE-2023-1389 (TP-Link) respectively. Both CVEs suffered from an OS command injection vulnerability.
Clop ransomware gang took advantage of the CVE-2023-0669 OS command injection vulnerability. It has been exploited as a zero-day to steal data from various companies worldwide.
A zero-day remote command injection vulnerability, CVE-2023-2868, has been exploited since 2022, for at least seven (7) months, to backdoor customers Barracuda Email Security Gateway (ESG) appliances. It was identified on May 19 2023. A custom malware was deployed to Barracuda ESG appliances with an ultimate goal to steal data.
Magniber ransomware gang group took advantage of the Security Bypass vulnerability,
CVE-2023-24880, in Microsoft Windows.
Nokoyama ransomware gang group took advantage of the CLFS (Common Log File System) driver Privilege Escalation vulnerability, CVE-2023-28252, in Microsoft Windows.
A Russia threat actor group, namely FIN7, took advantage of a design flaw vulnerability,
CVE-2023-27532, which affected the Veeam Backup software.
Threat actor groups, including UNC4857 and Lace Tempest, took advantage of a critical SQL Injection vulnerability, CVE-2023-34362, in the MOVEit Transfer, a secure managed file transfer software. Threat actors uploaded web shells with data exfiltration capabilities.
Vulnerabilities
In the following table we describe the vulnerabilities per vendor/product. Each row contains the following information:
CVE
Vendor
Product
PRIOn Score
Vulnerability Type
Threat Reports
Exploited in the Wild
Available exploits
Advisory (Patch/Info)
CVE | Vendor | Product | PRIOn Score | Vulnerability Type | Threat Reports | Exploited In the Wild | Exploits | Advisory (Patch/Info) |
|---|---|---|---|---|---|---|---|---|
Microsoft | Office | 99 | Privilege Escalation | YES (APT28) | CISA KEV Zer0-Day.cz GoogleProjectHero
| Github
| ||
PaperCut | NG | 95 | Bypass Authentication | YES (Bl00dy/Clop/LockBit) | CISA KEV | Coresecurity Labs Github ExploitDB | ||
Fortra | GoAnywhere MFT | 94 | Command Injection | YES (T505/Clop/LockBit) | CISA KEV Zer0-Day.cz
| Coresecurity Labs Metasploit Github ExploitDB
| ||
Microsoft | Windows | 94 | Security Feature Bypass | YES (Magniber) | CISA KEV Zer0-Day.cz GoogleProjectHero
| N/A | ||
Microsoft | Microsoft | 94 | Privilege Escalation | YES (Nokoyama) | CISA KEV Zer0-Day.cz GoogleProjectHero
| N/A | ||
Barracuda | ESG | 93 | Command Injection | YES (SALTWATER/SEASPY/SEASIDE) | CISA KEV Zer0-Day.cz
| N/A | ||
Zyxel | ZyWALL/USG/FLEX/ATP | 93 | OS Command Injection | YES (Mirai Botnet) | CISA KEV
| Github
| ||
Progress | MOVEit Transfer | 93 | SQL Injection | YES (UNC4857) | CISA KEV Zer0-Day.cz | N/A | ||
Chrome | 88 | Integer Overflow | N/A | CISA KEV Zer0-Day.cz GoogleProjectHero
| N/A | |||
Veeam | Backup & Replication | 86 | Design Flaw | YES (FIN7) | N/A | Coresecurity Labs Github
| ||
Microsoft | Windows | 86 | Privilege Escalation | N/A | CISA KEV Zer0-Day.cz
| N/A | ||
Chrome | 86 | Type Confusion | N/A | CISA KEV Zer0-Day.cz GoogleProjectHero
| N/A | |||
Apple | Multiple | 86 | Out of Bounds Write | N/A | CISA KEV Zer0-Day.cz GoogleProjectHero
| N/A | ||
Adobe | ColdFusion | 86 | Improper Access Control | N/A | CISA KEV Zer0-Day.cz
| Metasploit
| ||
Microsoft | Windows | 86 | Privilege Escalation | N/A | CISA KEV Zer0-Day.cz GoogleProjectHero
| N/A | ||
Microsoft | Windows | 86 | Security Feature Bypass | N/A | CISA KEV Zer0-Day.cz
| N/A | ||
Apple | Multiple | 86 | Type Confusion | N/A | CISA KEV Zer0-Day.cz GoogleProjectHero
| N/A | ||
Microsoft | Windows | 86 | Privilege Escalation | N/A | CISA KEV Zer0-Day.cz GoogleProjectHero
| N/A | ||
Sugarcrm | Sugarcrm | 86 | Input Validation | N/A | CISA KEV
| Metasploit
| ||
Microsoft | Windows | 85 | Remote Code Execution | N/A | CISA KEV Zer0-Day.cz GoogleProjectHero
| N/A | ||
Oracle | Weblogic | 85 | Design Flaw | N/A | CISA KEV
| Coresecurity Labs Github
| ||
Minio | Minio | 84 | Information Disclosure | N/A | CISA KEV
| Github
| ||
Ruckuswireless | Ruckuswireless | 83 | Remote Code Execution | YES (AndoryuBot) | CISA KEV
| N/A | ||
Apple | Webkit | 82 | Use After Free | N/A | CISA KEV Zer0-Day.cz GoogleProjectHero | N/A | ||
Apple | Webkit | 82 | Out of Bounds Read | N/A | CISA KEV Zer0-Day.cz GoogleProjectHero | N/A | ||
Apple | Webkit | 82 | Sandbox Escape | N/A | CISA KEV Zer0-Day.cz GoogleProjectHero | N/A | ||
ARM | GPU | 81 | Memory Leak | N/A | CISA KEV Zer0-Day.cz GoogleProjectHero | N/A | ||
TP-Link | Archer Ax21 | 80 | Command Injection | YES (Mirai Botnet) | CISA KEV | N/A | ||
Microsoft | Windows | 78 | Privilege Escalation | N/A | GoogleProjectHero | Coresecurity Labs Metasploit Github
| ||
Zoho | ManageEngine | 78 | Command Injection | N/A | N/A | Coresecurity Labs Github
| ||
Microsoft | Windows | 78 | Privilege Escalation | N/A | N/A | Coresecurity Labs
| ||
Debian | Sudoedit | 78 | Privilege Escalation | N/A | N/A | Metasploit Github
| ||
Microsoft | Windows | 77 | Security Feature Bypass | N/A | Zer0-Day.cz
| Github
| ||
Microsoft | Windows | 76 | Denial of Service | N/A | N/A | Coresecurity Labs
| ||
Microsoft | Windows | 76 | Privilege Escalation | N/A | N/A | Coresecurity Labs
| ||
Linux | Kernel | 75 | Use After Free | YES (Variston-Heliconia framework) | CISA KEV GoogleProjectHero
| N/A | ||
Noviservey | Noviservey | 73 | Remote Code Execution | N/A | CISA KEV | N/A | ||
Apple | Multiple | 71 | Use After Free | N/A | CISA KEV | N/A | ||
Android | 71 | Privilege Escalation | N/A | CISA KEV GoogleProjectHero | N/A | |||
Microsoft | Windows | 69 | Security Feature Bypass | YES (BlackLotus) | N/A | N/A | ||
Microsoft | Windows | 69 | Security Feature Bypass | YES (Russian Threat Actor) | N/A | N/A | ||
Papercut | NG | 68 | Bypass Authentication | YES (Clop/Lockbit) | N/A | N/A | ||
3CX | DesktopApp | 68 | Design Flaw | YES (Unknown Actor(s)) | N/A | N/A | ||
Samsung | Mobile | 63 | Security Feature Bypass | N/A | CISA KEV GoogleProjectHero
| N/A |
PRIOn Classification Recommendation
Patch Immediately (Score 100-85): 21
Must Be Patched (Score 84-75): 15
Should Be patched (Score 74-60): 8
Vendors
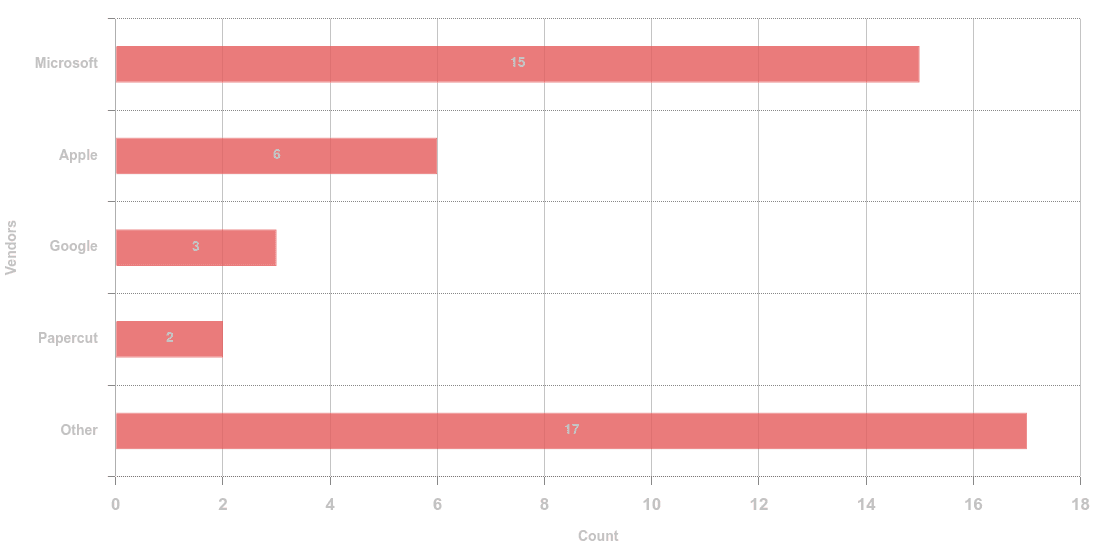
The following graph shows that 34.9% of the total disclosed vulnerabilities were reported in Microsoft products. The two closest ones were reported in Apple products with 14% and Google products with 6.98%.
Vulnerability Types
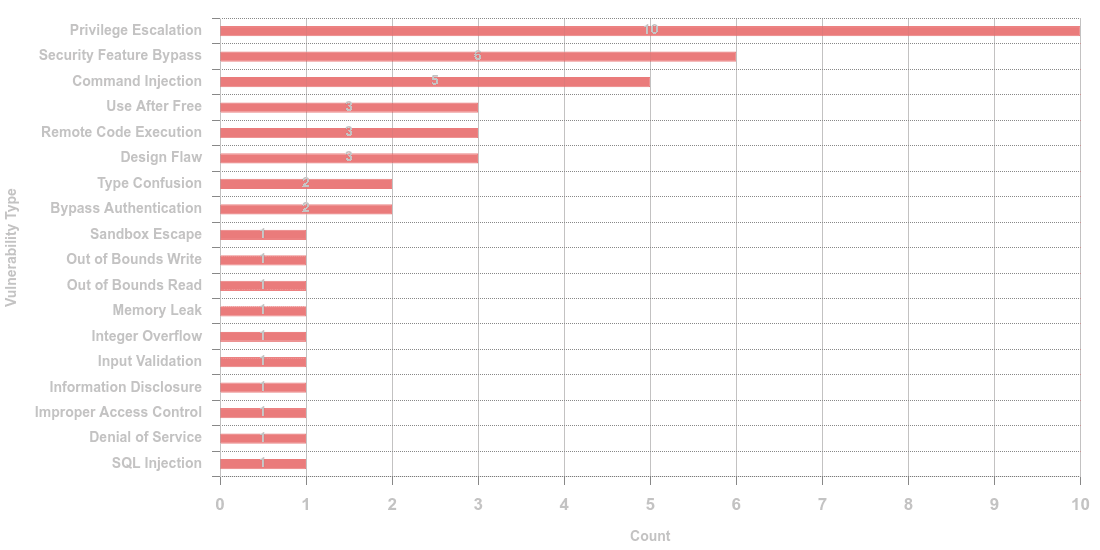
The following vulnerability types were extracted from the CVE descriptions via NLP classification techniques. Among them, Privilege Escalation, 22.7%, seems to be the number one vulnerability type. This vulnerability type allows unauthorized users to gain privileges, enabling them to access sensitive information or execute malicious activities. Security Feature Bypass is in the second place with 13.6%. Exploiting Security Feature Bypass vulnerabilities, threat actors can circumvent established (by design) security measures. In the third place we have Command Injection, 11.4%, critical vulnerabilities. By manipulating user input, attackers can execute arbitrary commands on vulnerable systems and gain unauthorized access to data. Other vulnerability types are memory corruption (e.g. Use After Free, Out of Bounds Read/Write, Type Confusion), Design Flaws, Input Validation, Authentication and Access Control issues etc.
Disclosed Vulnerabilities over Months
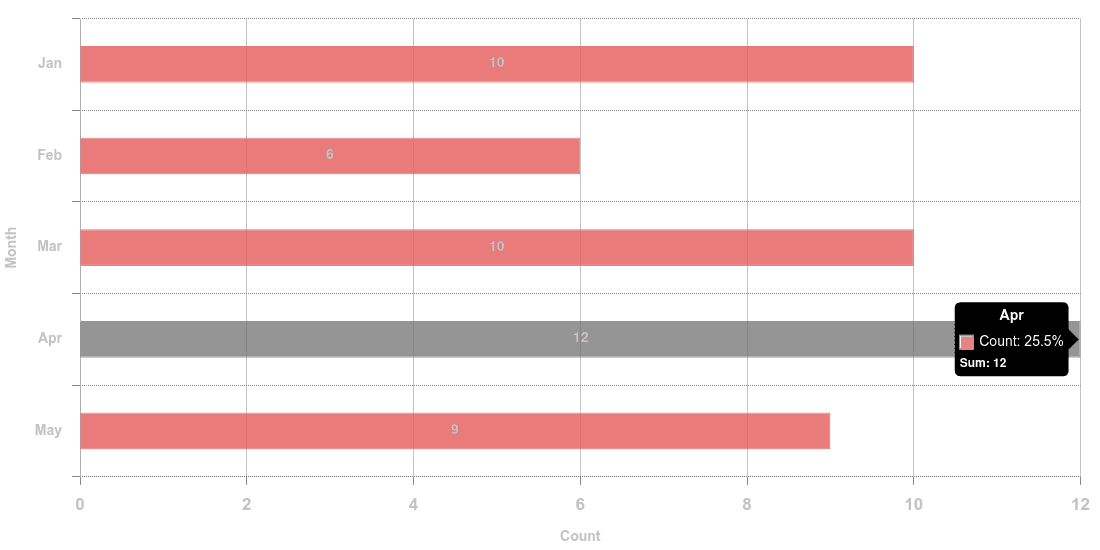
On this graph we can see the disclosed vulnerabilities per month. All months seem to be very busy in terms of exploitability, zero-days etc.
Thoughts
Understanding and monitoring vulnerability trends is crucial in maintaining robust cyber security practices. The evolving threat landscape demands constant vigilance and proactive measures from organizations and individuals alike. From the prevalence of privilege escalation vulnerabilities that enable unauthorized access to sensitive information, to the worrisome security feature bypass vulnerabilities that undermine established defenses, and the risks associated with command injection vulnerabilities that facilitate unauthorized execution of commands, it is clear that vulnerabilities continue to pose significant risks and evolve rapidly.The above analysis was done via the PRIOn Knowledge Base platform. PRIOn Knowledge Base, collects, enriches and analyses publicly disclosed vulnerabilities from the CVE program. It provides actionable data to cyber security practitioners to ensure that the most severe and dangerous vulnerabilities are prioritized. A risk score is assigned to each vulnerability according to its unique characteristics.Risk Based Vulnerability Management (RBVM) is one of the most challenging tasks in the cyber security landscape. We believe that a model that takes into account:
external contextualized data, such as threat and exploit intelligence, sentiment analysis on media presence
actionable extracted data from unstructured texts, using predictive Natural Processing Language techniques
internal business contextualized data (e.g. asset criticality, exposure etc.)
will enable companies to address vulnerabilities that could matter most to their environment. PRIOn could help your organization to triage and prioritize cyber security risks across your entire IT environment.
If you have any questions/comments/suggestions/corrections regarding the above analysis, feel free to contact us.